| Inputting Data Via Blinkenlights - Another Covert Channel |
| Written by Harry Fairhead |
| Sunday, 07 July 2019 |
|
You have probably heard that it is often possible to get data out of a system by monitoring the way status LEDs blink on and off, but now it seems the technique sometimes makes it possible to get data in as well. The story is that back in the good old days indicator lights were filament bulbs - inefficient and hot, but they had a good side. You could connect them to a line that pulsed and they glowed brighter the more high pulses. This provided an activity indicator with little effort. Things went slightly wrong when filament bulbs were replaced by modern LEDs. These were wired in the same way and glowed brighter the more high pulses, but now without the thermal inertia provided by the filament you could actually see the flickering caused by the pulses. Add a light detector, possibly with the help of a telescope, and you can read the data passing down the line. The ever popular blinkenlights could actually leak data.
No shortage of blinkenlights here! An IBM 360 control console. Taken a step further if you could infect the machine with some malware then you could drive LEDs that weren't connected to interesting data lines and open a covert channel to the outside world. Of course, the solution was fairly obvious - some tape over the offending LEDs may not look good, but it blocks the leak. A more sophisticated solution is to put a low-pass filter in anything that drives an LED so smoothing out the pulses to a varying DC. I can't say that I've ever seen this used in practice - even the few pence for a capacitor is probably more than most would tolerate when multiplied by the number of LEDs. Now we have some new research, from Joe Loughry of Lockheed Martin Space Systems and David Umphress of Auburn University, which shows how blinkenlights can become input devices. The big change that makes it possible is the almost universal use of GPIO - General Purpose IO - lines to drive LEDs. For a while one would include some sort of driver, a transistor or a driver in a chip. This makes the configuration hard-wired and the software can't do anything about the fact it is an output device. However, as time ticked on, GPIO lines and LEDs started to move together. GPIO lines could provide more current and LEDs needed less current until it was very thinkable to simply drive the LED directly from the GPIO line. It is even possible to use the built-in pull-up resistors in the GPIO hardware to avoid having to use an external current limiting resistor. You simply connect the LED to the GPIO line. With this change you have the possibility of reconfiguring what was intended as an output to be an input. General LEDs turn out to be light sensitive - they work in reverse. What this means is that malware can reprogram the GPIO line and start to read pulses of light focused on the LED. We have a two-way covert channel - but the machine needs to be infected with malware first.
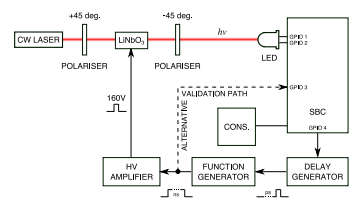
The proposed experiment This might make you feel safe - keep the malware out and everything remains secure, but there is another possible twist. It was discovered that even an LED connected as an output device can be used to drive the GPIO line higher or lower than its current logic level simply by shining a laser onto it. It generates a voltage even when in output mode. This overvoltage finds its way back into the machine and the suggestion is that this could be used to alter the internal state. This attack is similar to the "rowhammer" attack that has been slowly improved over time to allow specific bits in memory to be changed by repeated writing to adjacent memory locations. In this case the effect would be pseudo random because the exact timing of the pulse, and its interaction with the current state of the machine, would be difficult to predict. This is the next phase of the research - can we modify what a machine is doing in a coherent way by simply shining a bright light onto an LED?
More Information("Oops! Had the silly thing in reverse")---Optical injection attacks in through LED status indicators by Joe Loughry, University of Denver Information Leakage from Optical Emanations (pdf) Related ArticlesLED-it-GO: Leaking (a lot of) Data from Air-Gapped Computers via the (small) Hard Drive LED Rowhammer - Changing Memory Without Accessing It Experience the PDP-11/70 With Raspberry Pi To be informed about new articles on I Programmer, sign up for our weekly newsletter, subscribe to the RSS feed and follow us on Twitter, Facebook or Linkedin.
Comments
or email your comment to: comments@i-programmer.info <ASIN:1871962609> <ASIN:1871962455> <ASIN:1871962463> <ASIN:1871962617> |
| Last Updated ( Sunday, 07 July 2019 ) |