| Java Still Insecure Warns Homeland Security |
| Written by Alex Armstrong |
| Tuesday, 15 January 2013 |
|
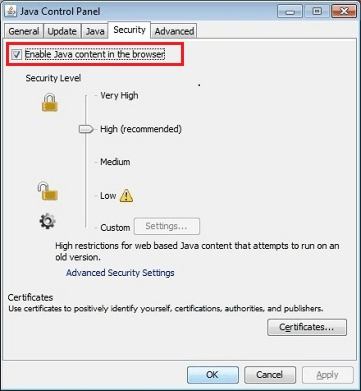
Oracle has issued a patch to remedy a security flaw in response to an urgent recommendation of the U.S. Department of Homeland Security to computer users to disable the Java plug-in. But is it enough and why is Java getting so much bad press recently? Java's ability to run the same code on multiple platforms, its "write once, run many" feature is a great advantage for developers - but it also gives hackers the same benefit. A security flaw discovered last week led to a posting on the website of the Homeland Security Computer Emergency Readiness Team (CERT) that warned: "Java 7 Update 10 and earlier contain an unspecified vulnerability that can allow an unauthenticated attacker to execute arbitrary code on a vulnerable system." Specifically, a remote attacker could convince a Web user to visit a specially made Web page, which could then carry out the attack. The attacking code could infect a well-known, legitimate site as well as ones with lesser credibility, and then stage the attack from there. Since there are no known practical solutions, the recommendation was that users disable Java in Web browsers. Oracle was quick to respond with Java 7 Update 11 which was released late on Sunday and changed the default security settings so that unsigned Java applets or Web applications now prompt for permission to run first, as opposed to the potentially dangerous previous behavior where they could operate without permission. According to the Update Release Notes: The default security level for Java applets and web start applications has been increased from "Medium" to "High". This affects the conditions under which unsigned (sandboxed) Java web applications can run. Previously, as long as you had the latest secure Java release installed applets and web start applications would continue to run as always. With the "High" setting the user is always warned before any unsigned application is run to prevent silent exploitation. CERT, however, responded by updating its Vulnerability Note to state: Unless it is absolutely necessary to run Java in web browsers, disable it ... even after updating to 7u11. This will help mitigate other Java vulnerabilities that may be discovered in the future. Instructions for disabling Java are provided on the main Java website and use feature introduced in Java 7 Update 10. Described as "a new security feature" it provides an option to disable Java in all browsers via the Java Control Panel.
Enable/disable option in Windows 8
There are also instructions to remove Java on specific browsers. Does the average user need Java? The advice is that most users don't although some businesses use it in the collaboration software GoToMeeting and it is required by some games.The use of applets has declined greatly since the early days of the web. Even websites that makes use of an applet usually provide an alternative way of working. As it is now relatively easy to switch on and off, probably the best advice to a user is to disable it and then wait to see what applications nag to to restore it. For the programmer the situation is very different. Java may not be used much on the client side, but it is heavily used on the server. Of course the current vulnerability doesn't have any impact for server side Java - however it does bring Java into disrepute. What is surprising is the number of times security flaws have been highlighted in the media since Oracle took over stewardship of the language. Java has always had security flaws, but suddenly it seems to be a top priority concern for everyone, including Homeland Security. One might almost conclude that there is an organized campaign against the language. Given that Oracle is in the process of trying to get Java accepted back on the client side with the introduction of the relaunched JavaFX, the fact that so many client side security risks make headline news is good material for a conspiracy theorist.
More InformationVulnerability Note - Java 7 fails to restrict access to privileged code Instructions for disabling Java Related ArticlesJava Is Top Attack Target Java FX 2.0 in the limelight at Java One
To be informed about new articles on I Programmer, install the I Programmer Toolbar, subscribe to the RSS feed, follow us on, Twitter, Facebook, Google+ or Linkedin, or sign up for our weekly newsletter.
Comments
or email your comment to: comments@i-programmer.info
|
| Last Updated ( Tuesday, 15 January 2013 ) |