|
Page 3 of 4
Step 3 - Calling our authenticated service with the AWS CLI
We've reached the stage where we finally can call our lambda, and we're going to do that with the AWS command line interface, an executable that we first have to download and install
After installation, we have to configure user's nikosvAuth profile on the local machine.For that we need the following pieces of information, all available from within the user's AWS Web console:
- the AWS Access Key
- the AWS Secret key
- the assigned AWS region
with those in place we fire the command line:
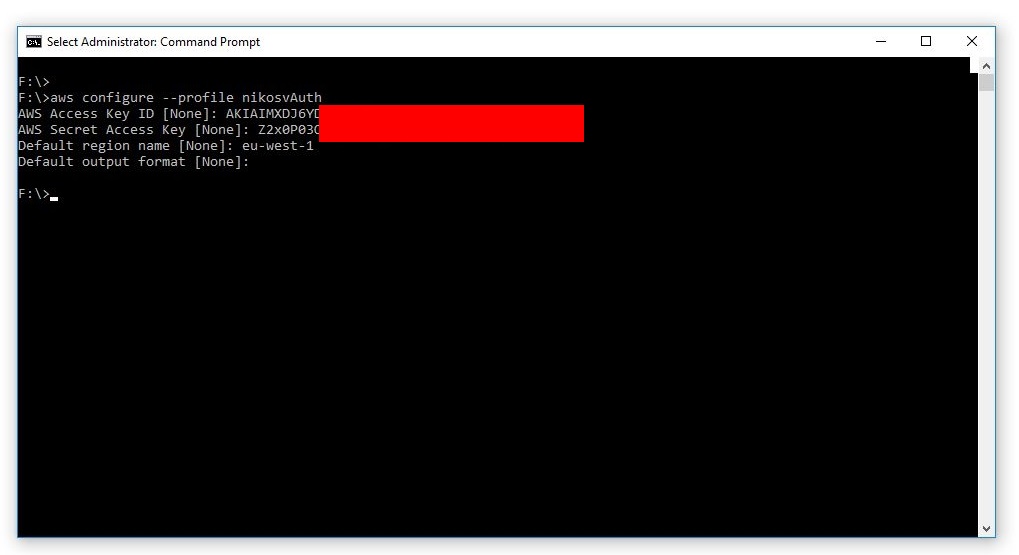
aws configure --profile nikosvAuth
and enter the all details we are asked for:
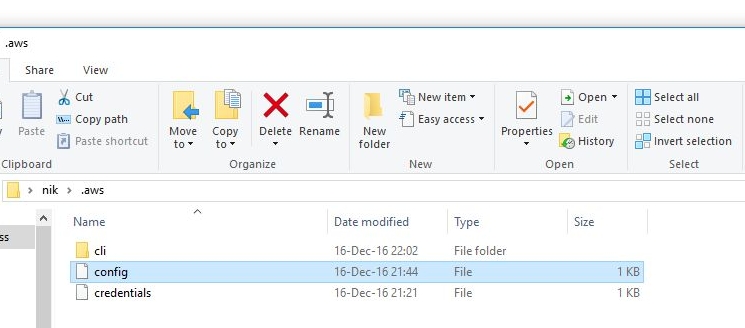
This generates an '.aws' directory under our local machine's user's home path, with one 'cli' sub-directory and two other files 'config' and 'credentials':
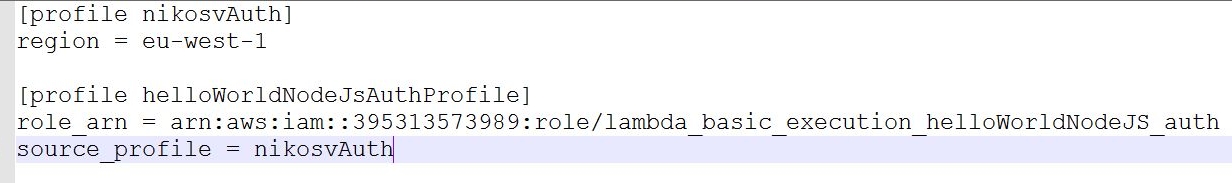
The next step is amending the 'config' file to hardwire the user/role relationship, by explicitly appending the role's profile details:
Now we're all set up and ready to ring our service, by feeding the command line with the payload, the profile to summon, the log-type to use and the 'outfile.txt' file to be written with the service's response:
aws lambda invoke --invocation-type RequestResponse --function-name helloWorldNodeJsAuth --region eu-west-1 --payload "{\"key1\":\"value1\"}" --profile helloWorldNodeJsAuthProfile --log-type Tail outfile.txt
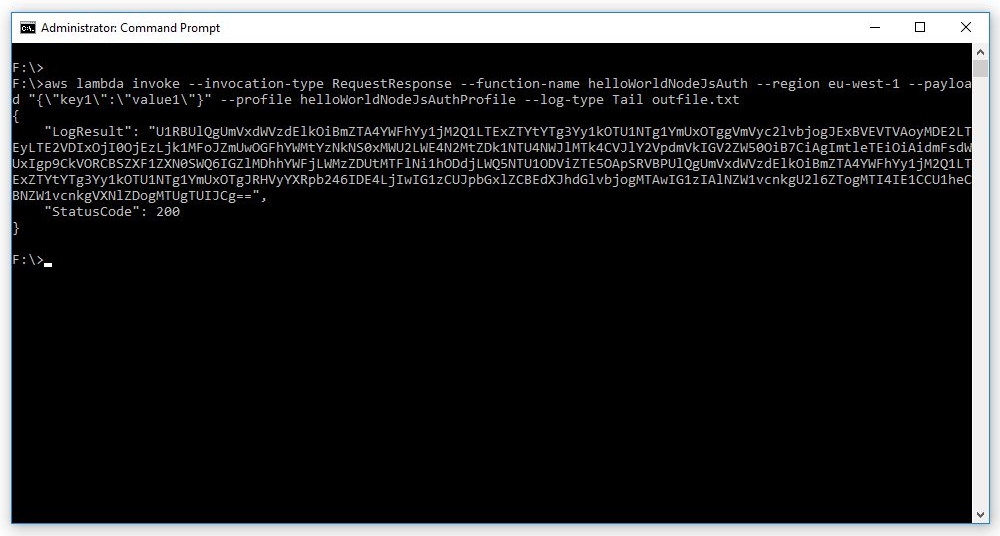
The resulting base 64 encoded string is the log's output.
To decode it, we copy it and feed it to any online decoding service:
an action that reveals the actual contents of the log's output:
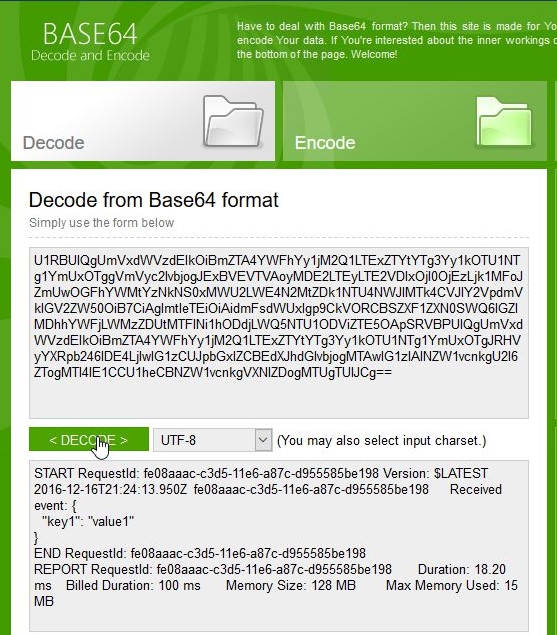
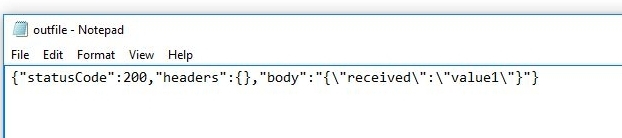
It seems everything went fine. We can further verify that this is actually the case by inspecting the contents of the 'outfile.txt':
Step 4 - Calling our authenticated service with HTTP requests
All fine but this procedure only holds true for use with the AWS CLI.To access the service through a pure HTTP endpoint like we did with the
lambda_basic_execution_helloWorldNodeJS function in the first part of the tutorial, we still have to do some tweaking.Essentially, grant executeable permissions on our API to our role.
Once more, through the AWS Web console and IAM Role menu, we create a new policy,
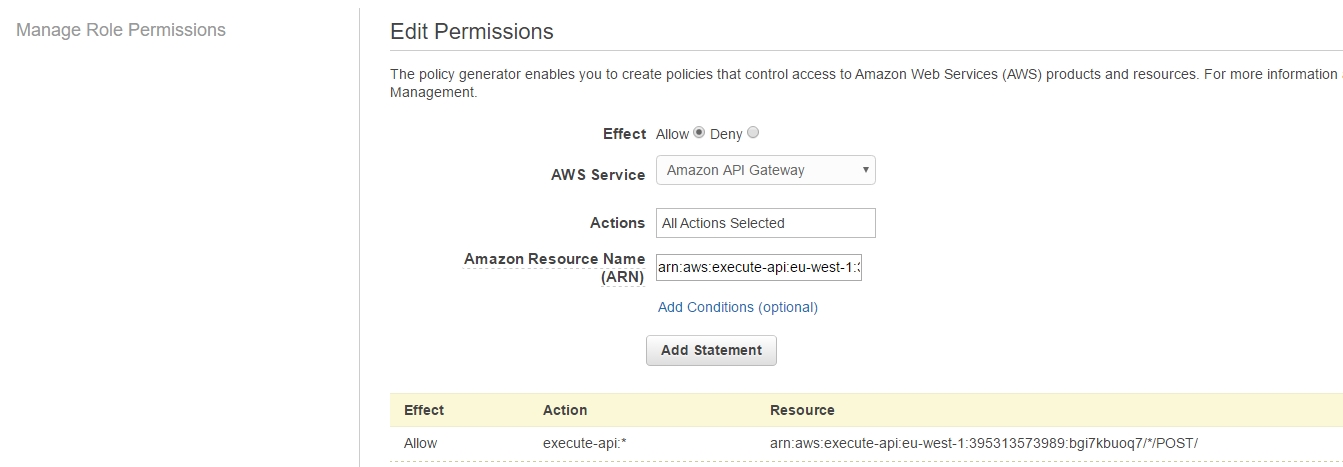
appending our endpoint's ARN to it,
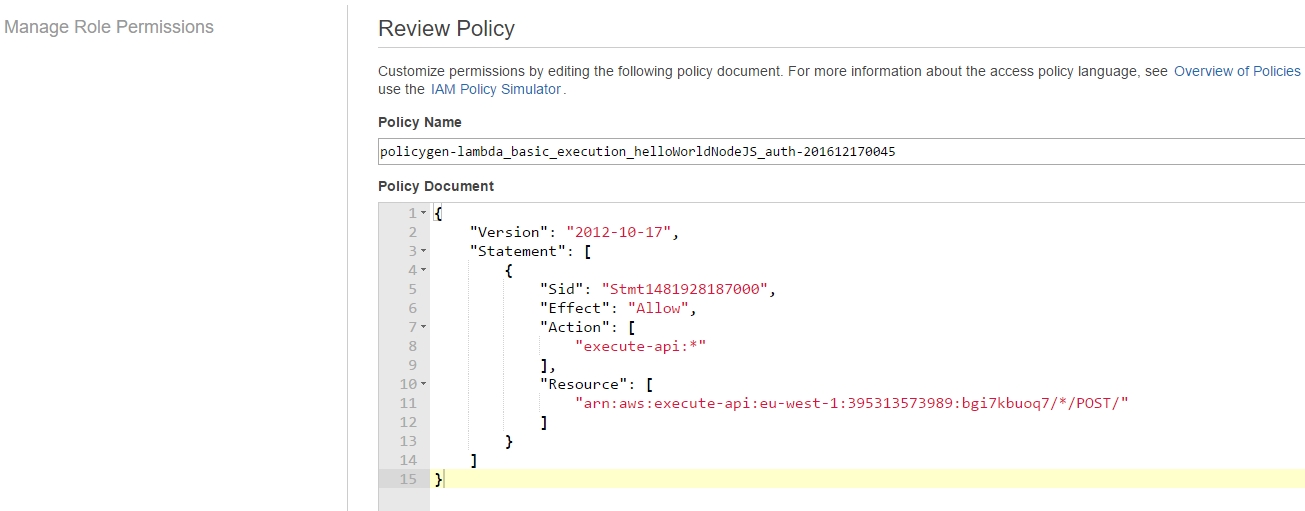
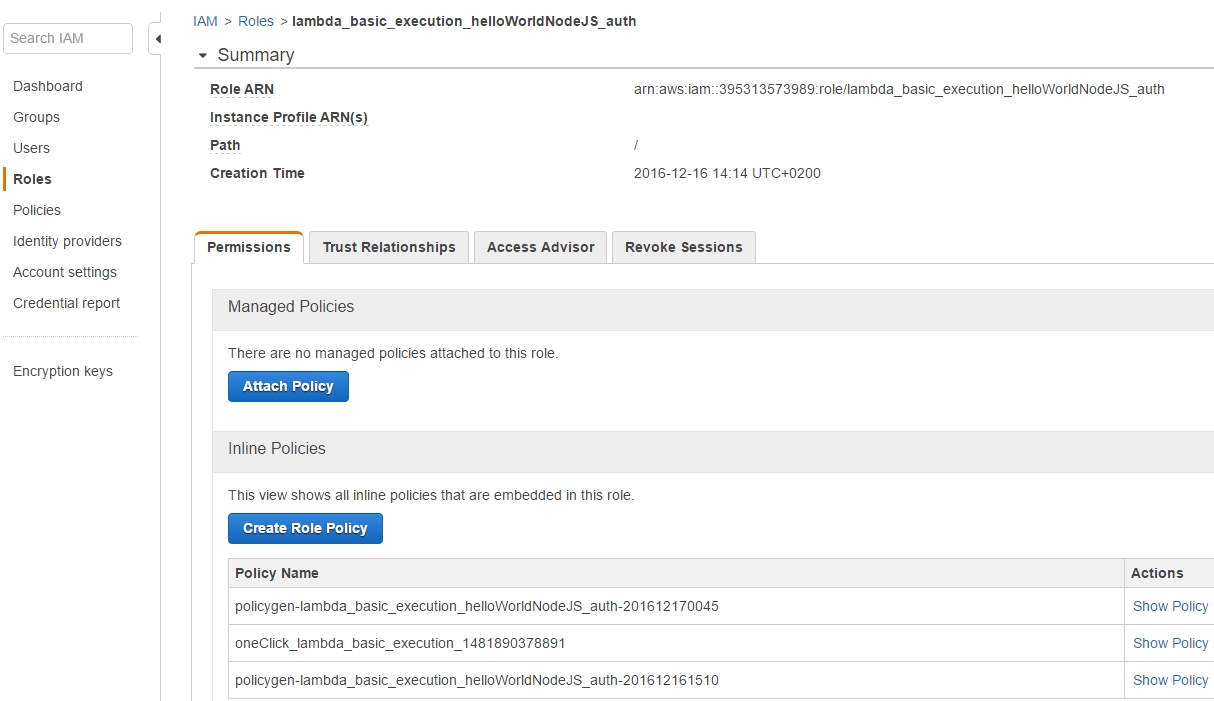
hence our role ends up with three attached policies.
|











