| Bearer - A New SAST Tool On The Block |
| Written by Nikos Vaggalis | |||
| Thursday, 06 April 2023 | |||
|
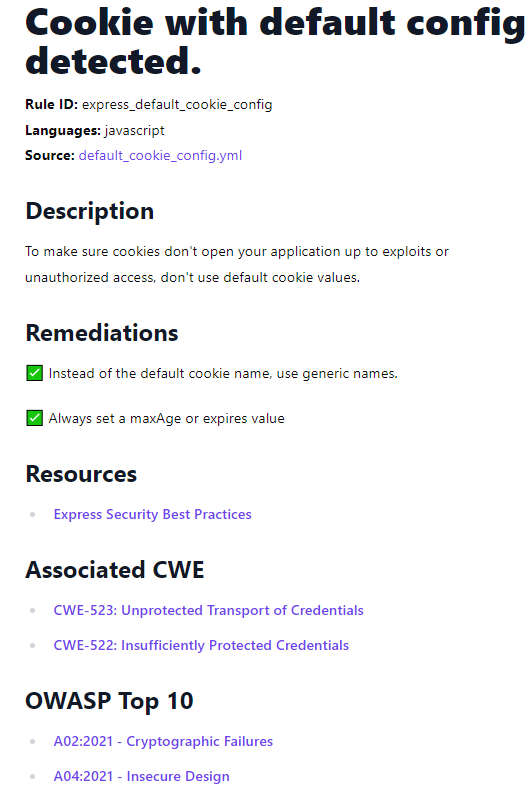
Bearer is a code security scanning tool (SAST) under secretive development for the last two years that discovers, filters and prioritizes security risks and vulnerabilities. Now it's ready and has been open sourced. Nowadays every company is a software house, regardless of the business it is in be it finance, manufacturing or healthcare. To provide value, businesses have to communicate through software applications built in-house or by a third party. The problem is that cyber attackers will attack those applications, probing them to uncover vulnerabilities to exploit and get access to your internal networks, steal company and customer data or just create havoc. These vulnerabilities occur because of bugs in the software and the most popular way in finding and fixing those bugs is by applying tooling like SAST to the source code. We've examined several such tools in the past like Semgrep and Qodana. Bearer is one of the most recent and modern additions to that family of SAST tools. Bearer assesses the OWASP Top 10 security risks and vulnerabilities found in today's Web Applications employing native filtering and prioritization based on their impact on sensitive data by following a rule set which at the time of writing includes more than 100 rules. Some practical examples of what kind of vulnerabilities Bearer under its rule engine can detect are:
Bearer's built-in rules are optimized for discovering the most most critical security risks and vulnerabilities of web applications and include corresponding Common Weakness Enumeration (CWE) and OWASP links to help in identifying them. That said, the rule set can be easily be extended under a rules notation DSL taking shape as simple yaml files.
Bearer comes with two types of security scanners, SAST (default) and Secrets. The SAST scanner is the default one if you don't specify any. This scanner uses the built-in rules to detect various security risks and vulnerabilities in your code. The Secrets scanner type detects hard-coded secrets in your code. It checks for common secret patterns such as keys, tokens, and passwords using the popular Gitleaks library. But that's not all;Bearer also discovers and classifies sensitive data by identifying patterns in the source code (not the values) by taking into consideration 120+ data types from sensitive data categories such as Personal Data (PD), Sensitive PD, Personally identifiable information (PII), Personal Health Information (PHI). Some of the categories of data that Bearer understands are:
The practicality of recognizing the presence of a sensitive data pattern in the source code is that, for example, you can be warned: if you are communicating an email address to an unsecured API or if you are using a weak encryption library in an application that processes any sensitive data as such averting a potential data breach or leak. As Bearer is a CLI tool, the quickest way to install it is with its install script:
There's also a Docker image and there's also a GitHub action in order to intergrate it into the CI/CD workflow. Afterwards, in order to scan your project, you point Bearer towards your project's directory with:
Once the scan is complete, Bearer will output a security report with details of any rules failures, as well as where in the codebase the infractions happened. As far as language support goes, Bearer currently supports JavaScript and Ruby and their associated most used frameworks and libraries, but more are on the way, such as PHP, Go, Python, Java, and C#. In closing, Bearer is certainly a noteworthy SAST tool, with its most valuable asset probably being the sensitive data patterns identification. As if that wasn't an incentive enough, then take account of its other great aspects, those of being free, open source and highly customizable. More InformationRelated ArticlesJetBrains Qodana Adds Taint Analysis For PHP Semgrep - More Than Just a Glorified Grep
To be informed about new articles on I Programmer, sign up for our weekly newsletter, subscribe to the RSS feed and follow us on Twitter, Facebook or Linkedin.
Comments
or email your comment to: comments@i-programmer.info |
|||
| Last Updated ( Thursday, 06 April 2023 ) |