| Codebreaking and Colossus |
| Written by Historian | ||||
Page 1 of 3
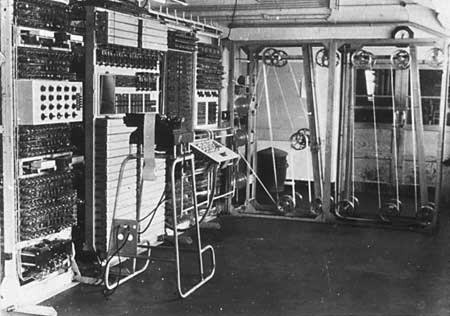
Colossus Colossus was operational in 1944 and is therefore in the running for being the world's the first electronic computer. However, its very existence, and the entire code-breaking effort based at Bletchely Park during World War II of which it was part, were shrouded in secrecy not only during its period of operation but for a long time afterwards. Information about its role in shortening the war by speeding up the deciphering of the top secret Lorenz/Tunny messages between Hitler and his generals, only came to light 30 years later. It took even longer, until 2000, for a report giving the full story of how the Tunny codes were broken and how Colossus performed its crucial role using thermionic valves originally intended for telephony to be declassified. The strange thing about keeping secrets is that when the truth is finally revealed it can be very difficult to put the past into its correct order. People actually like secrets because they help to bolster the popular conspiracy theories of the present. They also allow plenty of opportunity to embellish the truth when it is told years after the event. Once the entire story of Bletchely Park is pieced together, however, fact seems even more incredible than fiction. EnigmaOne of the first, and probably the best known, elements of the history is the cracking of the operational messages of the German military that were encode and decoded using electro-mechanical cipher machines that relied on the position of rotors to scramble messages.
An Enigma coding machine
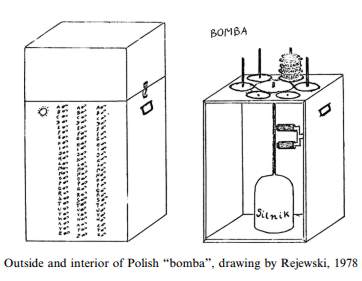
On hearing of the Enigma coding machines, often in tandem with Alan Turing, who has been given the accolade "father of computer science" you may assume that the task of breaking the code was a matter of advanced cryptography and super computers. The fact that it was all kept secret for so long encourages this conclusion - after all why keep irrelevant 1940's technology secret? The truth of the matter is rather different. To start off with there is a Polish prequel to the British account of Enigma codes being cracked at Bletchley Park. As early as 1932, three mathematicians from Poland's General Staff Code Bureau, Marian Rejewski, Jerzy Różycki and Henryk Zygalski, deciphered the mathematical basis of the Enigma, constructed a copy of the coding machine, and started to read German secret dispatches. Several more copies of the Enigma machine were built the following year. Marian Rejewski deduced the internal wiring of the Enigma and constructed a cyclometer, which consisted of two Enigma machines side by side with their right hand wheels offset by three places. This solved the problem of Enigma's constantly changing keys, rotating disks and electrical connections. Rejewski went on to devise the "bomba kryptologiczna" or Bomba, designed to overcome the double encypherment of the message setting that the Germans had introduced. Another aid to decryption of the double enciphered message settings, the Zygalski Sheets, were perforated overlays which produced more reliable results than the Bomba
In July 1939, with the invasion of Poland imminent, the Polish cryptographers decided to share their work with the French and British code breakers. They handed over copies of the Enigma machine and revealed the details of the Cyclometers, Bombas and Zygalski sheets. Armed with this knowledge, Alan Turing and Gordon Welchman, both recruited at the start of World War II as members the UK Government Code and Cypher School based at Bletchley Park, designed a machine they called the Bombe, acknowledging the work of the Poles. It was an electromechanical device built by Harold Keen and engineers at the British Tabulating Machine Company. Bombes were used, according to Gordon Welchman: "simply to reduce the assumptions of wheel order and scrambler positions that required 'further analysis' to a manageable number". This involved discovering the daily settings of the Enigma machines on the various German military networks: specifically, the set of rotors in use and their positions in the machine; the rotor core start positions for the message and the stecker partner of a specified letter for a set of wheel orders. Manual techniques were then used to complete the decryption process. Over the course of their operation Bletchley Park 210 Bombes helped decode up to 5,000 intercepted message per day. At the end of the war all the Bombes were dismantled but a a fully-functioning replica was completed in 2007 a fully-functioning replica was completed in 2007 and is on display at Bletchley Park as shown in this video, from around 5:00:
Why was Enigma so easy to break?The Germans had a very good coding machine in the Enigma but they failed to ensure that it was used properly and they believed in its invulnerability just too much. The mistakes that they made are, from a more modern and sophisticated perspective, incredible - but don't be too smug because they also read like a list of today's most common security errors! In principle the task of breaking the Enigma code was next to impossible. To crack an encrypted message would involve trying over 200 million, million, million possible keys - assuming that you knew the way that the Enigma machine was wired up. Fortunately, thanks to the Poles and to other espionage the code breakers at Bletchely Park did have insights into the wiring, but the problem still seemed to be impossible. Indeed if the Germans had not made mistakes in the use of the machine it would have been very difficult to make progress and even more difficult to prove to anyone that the resources should be dedicated to cracking the code - after all why attempt the impossible. The mistakes made in using the Enigma are a catalogue of simple human errors. The first mistake was in always coding a three letter "discriminant" twice at the start of every message. This gave the code crackers an example of three letters and two of their possible codings. A similar mistake was to always use very standard and very long addresses within their messages. They also never varied the content of their common messages. For example remote stations would often send "Nothing to report" messages which provided perfect material for any attempt to find the key currently in use for these and more important messages. By using these known parts of encrypted messages, "cribs" in the jargon of the time, the problem of finding the key chosen for the day was possible and once you had the key you could read all of the other traffic. One amazing lapse of good operating practice happened early on in the war. The German clerk in charge of making up "random" keys to be used each day obviously got bored with the tedious task. Instead of generating new keys for each day he went back to the key book used for the previous year. Once the code breakers noticed this fact obtaining a single key for the day allowed them to look up the other keys used in conjunction with it the previous year. In other words, breaking a single key allowed them to read every message for the entire day! As the war progressed the German's did tighten up on their procedures but the early lapses gave the British code breakers the information and headstart they needed to keep up with the situation.
<ASIN:0947712364> <ASIN:019284055X> <ASIN:1843543311> |
||||
| Last Updated ( Monday, 27 November 2023 ) |