| VPN - Virtual Private Network |
| Written by Harry Fairhead | |||
| Monday, 04 July 2011 | |||
Page 1 of 2 A Virtual Private Network, or VPN, is an easy and low-cost way of connecting to your home or company network from anywhere in the world with all of the facilities that a local connection would bring.
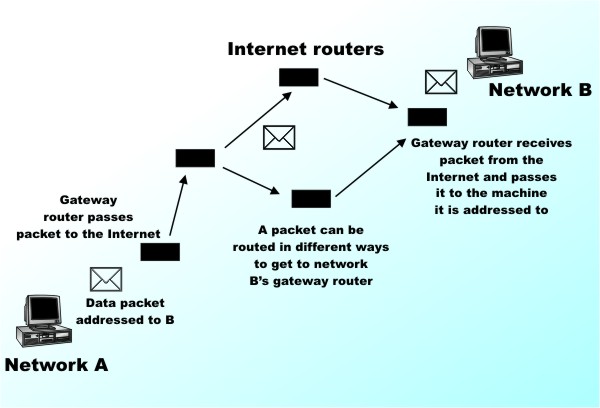
How can anything private be virtual – the jargon doesn’t seem to make a lot of sense but the idea does. A Virtual Private Network, or VPN, is an easy and low-cost way of connecting to your home or company network from anywhere in the world with all of the facilities that a local connection would bring. VPNs can even be used to connect two private networks, say two branch offices or two home networks, together, making them behave like a single entity. Of course all of this is possible if you buy or rent a hardwired connection between the two things you want to connect, but the key point is that the VPN alternative can be very cheap. In fact, if both ends of the connection have broadband then there might well be no additional cost to joining the two together because a VPN uses the Internet to make the connection. A VPN can also be used to provide a measure of security and anonymity beyond what is possible on the public internet. So how does it all work? The virtual circuitThere are many ways to think about VPNs according to the particular use you have in mind. At the bottom of it all, however, is the idea of using the Internet to transfer data between two specific locations as if it was a cable connecting the two – a so-called "virtual circuit". This doesn’t sound very different to what the Internet usually does, but it is. The Internet Protocol (IP) works by routing packets of data from source to destination. Each packet has a destination address and, each time it reaches a router, the router works out where to pass it to so as to get it nearer to its destination. What this means is that when machine A sends a data packet to machine B it can’t know, and usually doesn’t care, what route the packet takes. This is what makes the Internet flexible but it also makes the Internet insecure.
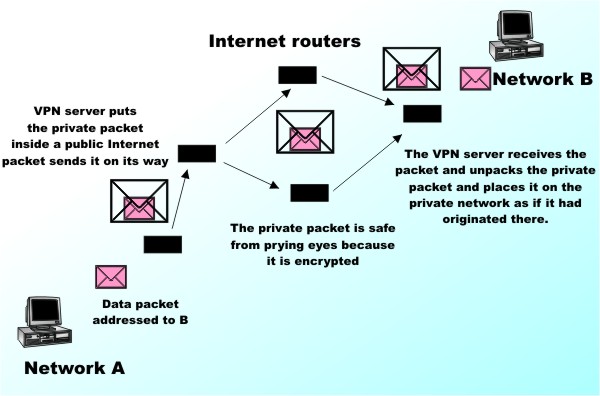
Local private networks often use the same method of transferring data as the Internet but they keep the packets within a known group of machines and addresses. When there is a need to exchange packets with the Internet they are routed though a gateway and on to the outside world. VPN uses this idea to make point-to-point communication secure by embedding private network packets within public Internet packets. The key to the security is that the private packets are encrypted within the public Internet packets. In theory when a machine on private network A wants to send a packet to a machine on private network B the packet is accepted by the VPN server. It is then encrypted and encapsulated within a standard IP packet that has a destination address corresponding to the VPN server at network B. Notice that both VPN servers have to have to be “on the Internet” in the sense of having publicly accessible IP addresses. When the packet arrives at network B’s VPN server it extracts the encapsulated private packet, decrypts it and sends it on its way within the local network.The machines within network A and B don't have to have publicly accessible address - that is they don't have to be on the public Internet. This way of using the public Internet to connect two machines that are not on the public internet is another advantage of the VPN approach. As far as users of network A and B are concerned the VPN is as good as a dedicated physical connection. The idea of using public data packets to transfer embedded private data packets is often called “tunnelling” because it seems to create a data tunnel between the two networks.
To be accurate the type of VPN just described is more properly called an IP VPN because there were VPNs before the Internet was popular. In general the idea of tunnelling can be used to encapsulate any passenger protocol in any carrier protocol. However as the majority of private and public networks use the Internet Protocol (IP) the most common situation is IP packets carrying other IP packets. Notice that while the VPN servers have to have public IP addresses so that data can be sent from one to the other via the Internet not only do the machines on the private networks use private IP addresses they can even use some protocol other than IP. Currently there are two main standards for such “IP tunnels” – PPTP and L2TP/IPSec – and these control the way the data is encapsulated in the carrier protocol. These protocols are in fact based on another, older, protocol called PPP or Point to Point Protocol. This is in wide use to connect a client machine to the Internet via a dialup line or even a broadband connection. Microsoft, 3COM, US Robotics and others, took the obvious step of generalising PPP to product Point-to-Point Tunnelling Protocol or PPTP. The main objection to PPTP is that it’s proprietary and there have been doubts about various aspects of its security in the past – but this has been improved in successive upgrades. As you might well guess, being a Microsoft-originated protocol it is well supported on all versions of Window from Windows 98 to the latest version. The second most common VPN protocol, Layer 2 Tunneling Protocol (L2TP), is an Internet Engineering Task Force (IETF) standard and as such many regard it as better designed for the job, and specifically more secure, than PPTP. L2TP uses Internet Protocol Security, or IPSec, for encryption. This is a very flexible standard that should be capable of meeting almost any security requirement. The only real problem with L2TP/IPSec is that it is more complex.
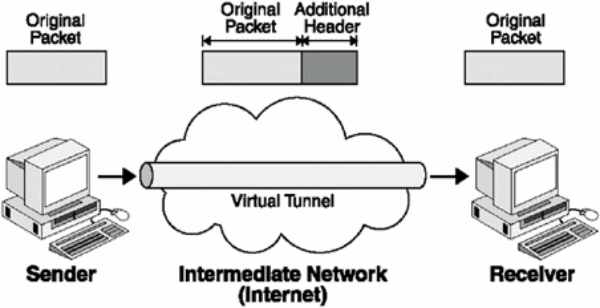
VPN protocols add extra headers to the original data packet |
|||
| Last Updated ( Friday, 25 February 2022 ) |