| AWS Lambda For The Impatient Part 2 |
| Written by Nikos Vaggalis | |||||
| Monday, 23 January 2017 | |||||
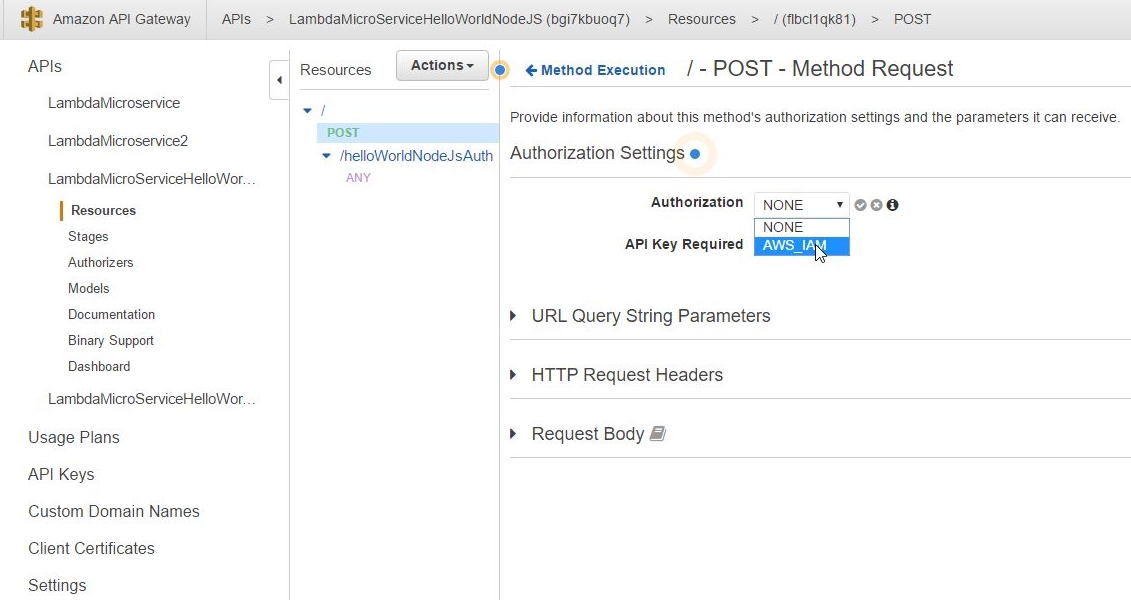
Page 1 of 4 In the first part of the AWS Lambda for the Impatient tutorial series we set out to create our very first lambda function and call it through an open, public, unrestricted and unauthenticated endpoint.This time around we add security so that calling our lambdas will require the client to authenticate through an IAM Role and User name.
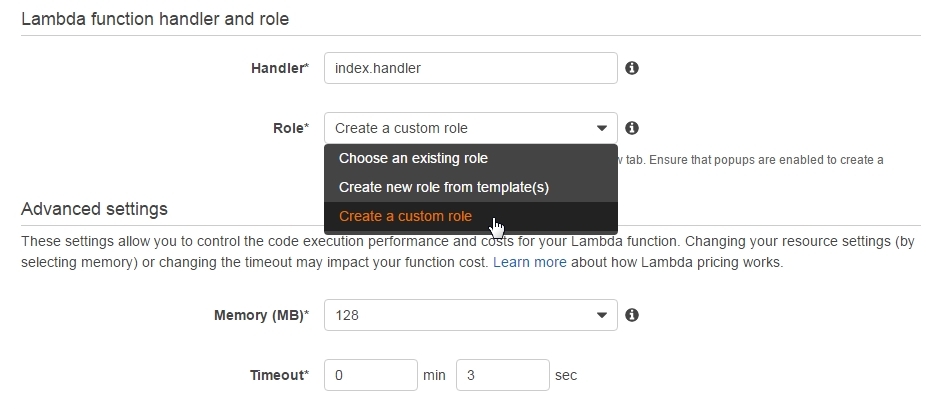
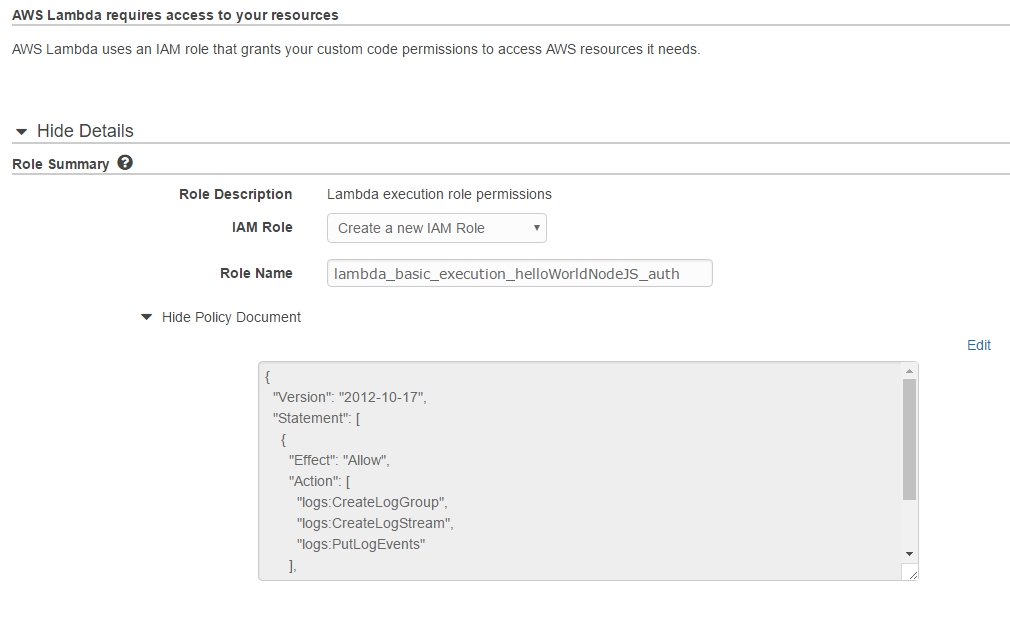
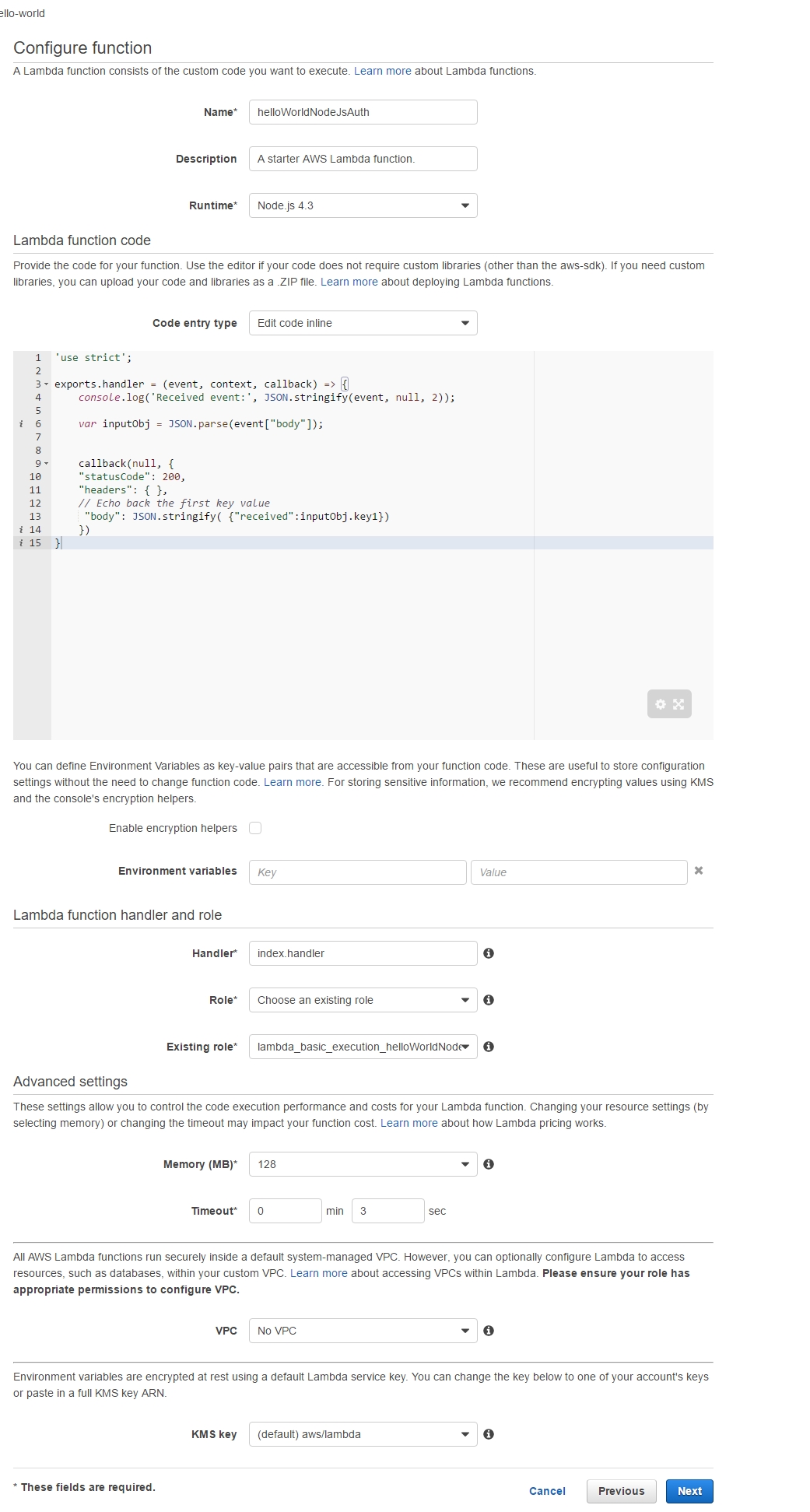
Step 1 - Create a new Lambda function and API Gateway endpoint As happened in the first part, we create a new lambda called lambda_basic_execution_helloWorldNodeJS but with the added suffix of _auth. So that we can tell it apart, call it lambda_basic_execution_helloWorldNodeJS_auth. Despite the name change, the function's code remains the same as last time: use strict'; var inputObj = JSON.parse(event["body"]);}
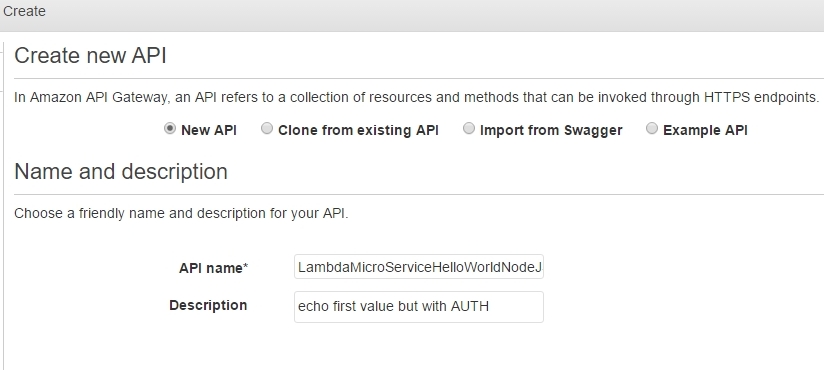
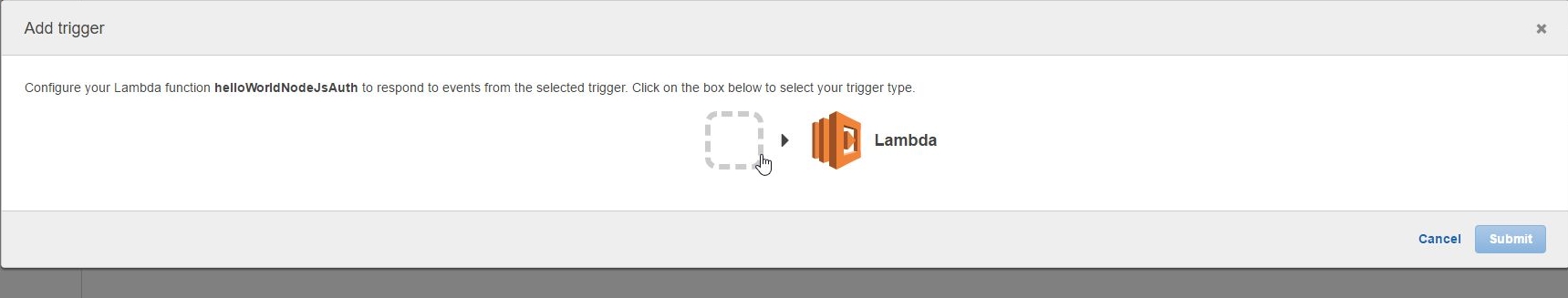
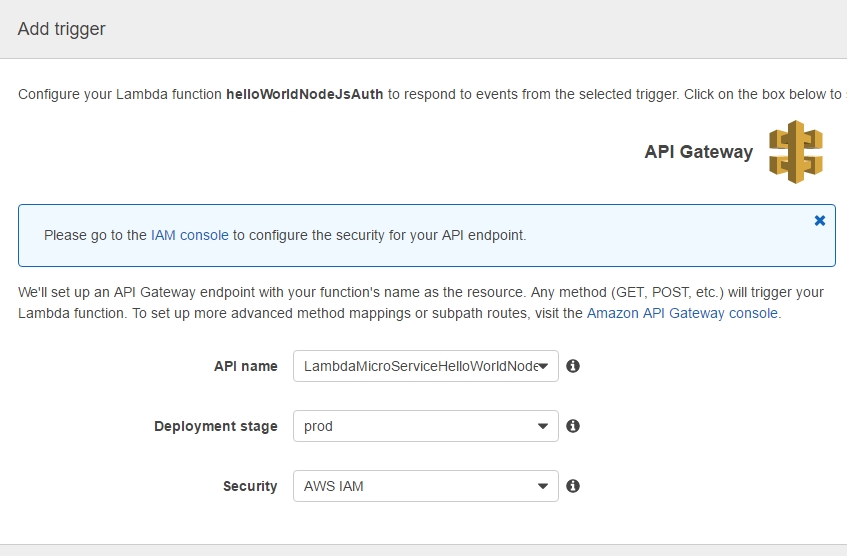
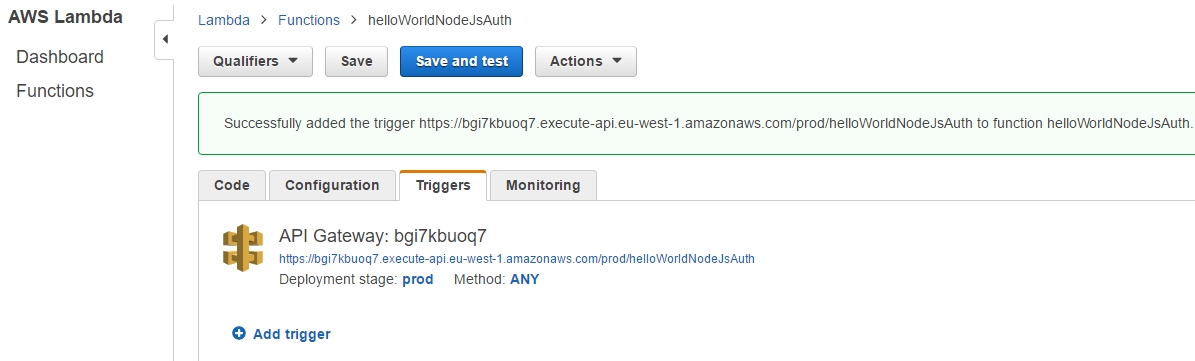
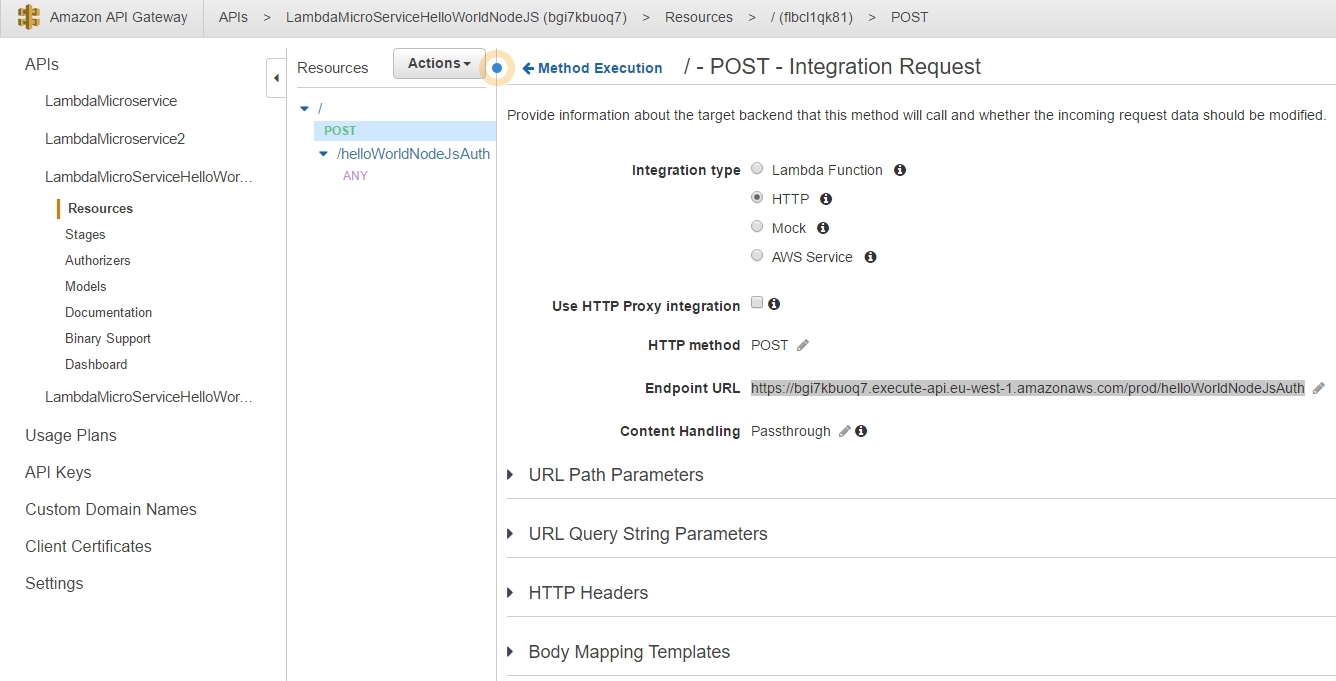
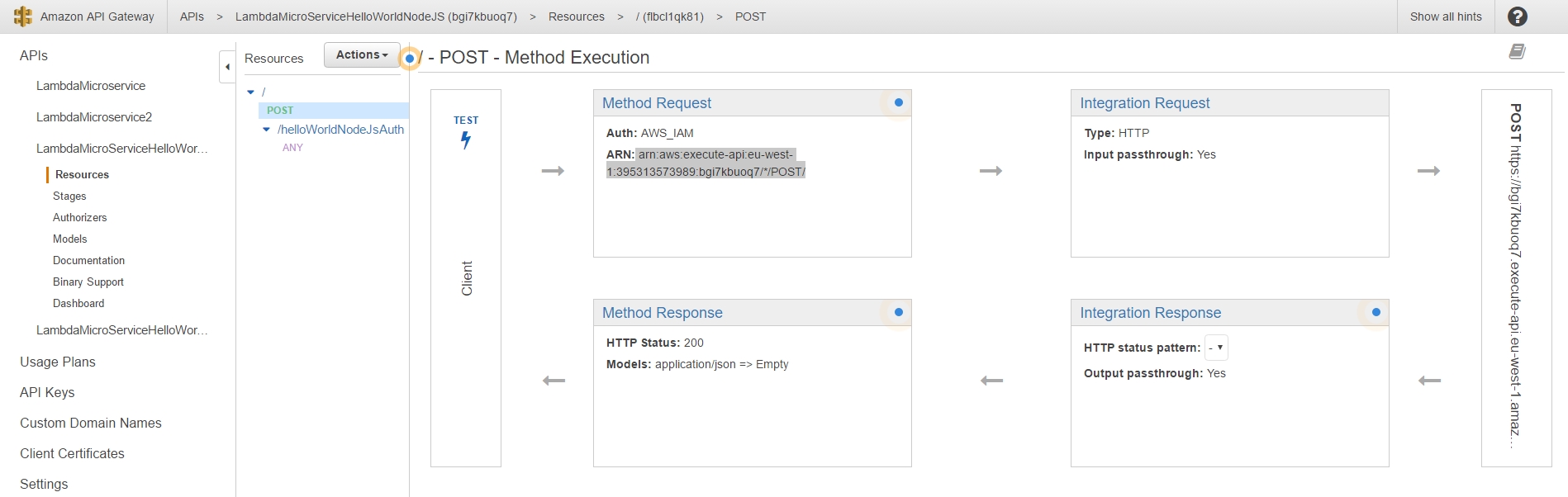
Back to our lambda_basic_execution_helloWorldNodeJS_auth function in order to continue adding a new Trigger: Next we need to go back to the API Gateway and the LambdaMicroServiceHelloWorldNodeJSAuth API. This time we are going to define the HTTP methods that our API will listen to as well as how to react to their invocation. As lambdas work only with POST requests, we add just the POST method: |
|||||
| Last Updated ( Sunday, 19 February 2017 ) |