| Coded Easter Eggs |
Page 1 of 3 A software Easter Egg is an intentionally hidden novelty or message concealed for personal reasons within a computer program or application. We take a look at its history and original motivation and see how things changed when Googlers expanded the tradition. The original version of this article was posted on Easter Sunday, 2011. This version is updated to Easter Monday, 2022. What Constitutes a Software Easter Egg?In order to be counted as an Easter Egg, rather than a bug or a glitch the feature has to satisfy the following criteria: 1. Be entertaining and in no way harmful 2. Be undocumented and unexpected but reproducible - Easter Eggs are concealed features that are not a normal part of the product but can be made to work by all users given the instructions and for the first few years but not necessarily any longer in 2022: 3. Deliberate inclusions that have a personal significance for the programmer The whole Easter Egg idea is a strange one. Usually programmers are usually hard pressed to create the code that they actually need and the notion that they have time for fun and games goes beyond the call of duty. There is also the small problem that the dividing line between an Easter Egg and malicious code is a fine one. A programmer working in a team not only has to hide the code from the end user but from his fellow programmers and his employer. When a user finds an Easter Egg it must suggest that there are things hidden in the code and this doesn't sit well with the idea of secure computing. If you can hide an Easter Egg then why not a backdoor into the program? The First Easter Egg?The term Easter Egg referring to a hidden message within computer software dates back to 1979. It was first used by Atari after Warren Robinett, the designer of Adventure, a cartridge-based video game for the Atari 2600, included a hidden surprise within it
Adventure was published in 1978 and sold 1 million copies at $25 retail - but its designer who was paid a salary of $22K per year didn't even get to have his name in the credits. It was a desire for recognition that prompted Robinett to add a secret room where he included his signature. The desire for recognition continued to be a common motivation for adding an easter egg over the following years. Years later Robinett created a PowerPoint presentation on how he designed the game to fit the hardware constraints of the Atari 2600 which provided 4096 bytes (4K) for the game code and included a slide that revealed the secret room:
Asked by James Hague for his collection Halcyon Days: Interviews with Classic Computer and Video Games Programmers why he decided to hide his name in this way Robinett explained: Each 2600 game was designed entirely by one person. But on the package it said basically "Adventure, by Atari." And we were only getting salaries, no cut of the huge profits. It was a signature, like at the bottom of a painting. But to make it happen, I had to hide my signature in the code, in a really obscure place, and not tell anybody. Of course, an adventure game, with multiple rooms, is perfect for secret things, because it's easy to make extra rooms that are really hard to get into. After Robinett handed over the final version of the program, Atari manufactured and distributed several hundred thousand cartridges. By the time the secret room containing the signature was discovered Robinett had already left Atari. What surprised him was that when a 15 year old from Salt lake City wrote a letter to Atari about his discovery of the secret room, rather than react negatively, Steve Wright, Director of Software Development at Atari referred to the hidden surprise as an "easter egg" and not only claimed that he thought it added value to the game decided to make it company policy to include concealed features in future games. Once Atari had coined the term "easter egg" for this practice, evidence of earlier examples came to light. For example in the games Video Whiz Ball and Alien Invasion produced for the Fairchild Channel F, a games console released by Fairchild Semiconductor in 1976, certain combinations of keystrokes reveals of the names of the programmers. MicrosoftEarly products from Microsoft were responsible for continuing this tradition of concealed names and of cameo appearances. The Microsoft Bear was the mascot of the Windows 3.1 team and cropped up in two Easter eggs in Windows 3.1.
Other Microsoft Easter Eggs were treats for the users who managed to find them. Excel was the Microsoft product best known for this with small games concealed in every version from Excel 5.0 to 9.0. The first was "The Hall of Tortured Souls" described as a "Doom-like mini-game". To access it you had to do the following:
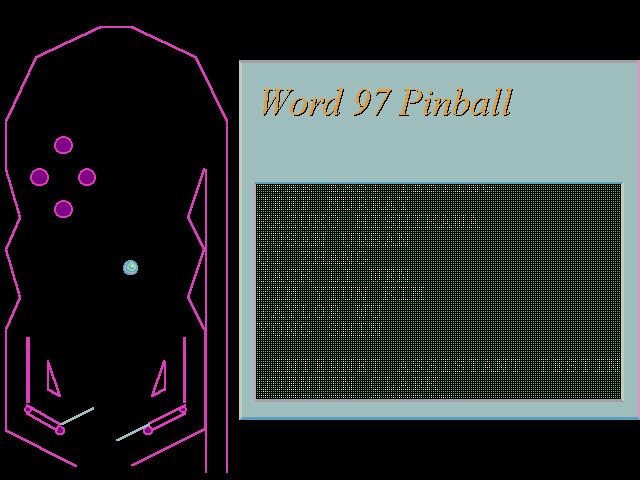
Office 97 had games in all three of its main components. Excel contained a hidden flight simulator, Access had a simulation of the Magic 8-Ball fortune-telling toy and Word contained a pinball game:
In time-honoured tradition, a list of developer names is "hidden" in Excel 2000 (Excel 9). The following sequence of steps are required to see them scroll up the screen:
Officially Microsoft stopped including Easter eggs in its programs as part of its Trustworthy Computing Initiative in 2002 which was intended to address concerns about the security and reliability of previous Microsoft Windows - but rather backfired in that it heightened customers suspicions about software quality. Easter Egg were later reintroduced with a game of Asteroids in the Notifications application of Office 2004 Mac and in Outlook 2010 the default picture for new contacts is a silhouette of Bill Gates.
|
||||
| Last Updated ( Tuesday, 19 April 2022 ) |


 The About box gives the email alias of Brad Silverberg who was in charge of Windows production and three other email aliases billg (Bill Gates), steveb (Steve Ballmer) and t-bear (teddy bear) appeared together in a Special Thanks section.
The About box gives the email alias of Brad Silverberg who was in charge of Windows production and three other email aliases billg (Bill Gates), steveb (Steve Ballmer) and t-bear (teddy bear) appeared together in a Special Thanks section.