| Five Things Developers Can Do To Address MitM Attacks |
| Written by Jeff Broth | |||
| Monday, 12 June 2023 | |||
|
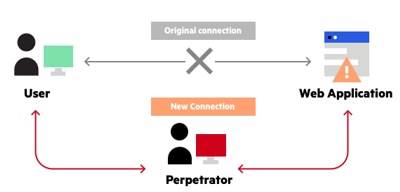
A man-in-the-middle (MitM) attack is a cyber attack where the attacker secretly intercepts and relays messages between two parties who believe they are communicating directly with each other. You can think of it as the equivalent of a mailman opening your bank statement, writing down your account details and then resealing the envelope and delivering it to your door. Traditionally, man-in-the-middle (MITM) attacks, particularly the so-called Evil Twins attack, entail the deployment of a bogus access point (AP) to hijack traffic. This no longer seems to be the case. Last month, researchers from George Mason University, Tsinghua University, and Zhongguancun Lab published a paper revealing a man-in-the-middle (MITM) attack that does not use a rogue AP. This development has significant consequences, particularly in the way security controls work. Modern Wi-Fi networks typically employ WPA, WPA2, or WPA3 protection. These have been effective at addressing the MITM threat. However, the emergence of a MITM attack that does not require a rogue AP throws these conventional defenses off. The researchers said that they tested 55 wireless routers from ten popular brands, and none of them managed to detect the anomaly. Cyber attacks are evolving and cybercriminals will find new ways to breach security controls. It is unwise to fully rely on security solutions. Cybersecurity should follow a holistic approach that Ensure all communications are secureOne of the most important contributions of developers to the fight against MitM attacks is the compulsory use of secure communications. The apps they produce should only allow client- Additionally, developers can enable perfect forward secrecy (PFS) Applications can use this encryption system as a backup plan against the possibility of the server’s private key getting
Moreover, developers can enforce mutual authentication, wherein both the server and client are required to authenticate their identities before any communication or data transmission happens. This is usually done through the generation and distribution of certificates to both the server and client, proper server and client configuration, and SSL/TLS handshake. Use strong encryptionEncryption is a basic requirement for overall cybersecurity and should be applied to data both at rest and in transit. When it comes to combating MITM attacks, though, the focus is on In addition to using formidable encryption algorithms, it is also vital to have a robust key management system. This means that strong keys should be generated, securely stored, and rotated regularly. The keys are vital for decryption, which means that if threat actors manage to know them, the protection afforded by encryption quickly falls apart. On the other hand, developers play a role in securely managing encryption and decryption operations. They have a hand in making sure that encryption/decryption operations are only Make the most of certificatesIn line with the need for secure communications and encryption, it is also important to pay attention to certificates. These indicate the use of encryption to protect data. Web browsers and apps automatically check website certificates to make sure that they are valid. If they detect validity issues, they present a dialog box that indicates the error and cautions users from accessing a site or web app. Developers have control over proper certificate validation, so they should be enforcing it. Server certificate validation should include the verification of the certificate chain, the inspection of the In addition to certificate validation, it is also advisable to foster certificate transparency by enabling certificate transparency logs. These logs create publicly accessible and auditable records of the certificates issued. They are useful in detecting unauthorized certificates, which means they can aid the detection of potential MITM attacks. Also, it helps to implement certificate pinning, the process of hardcoding specific certificates or public keys exclusively to a specific domain. Doing this helps reduce the risk of being deceived into accepting compromised certificates, which means avoiding possible MITM attacks. Get involved in regular security auditsMan-in-the-middle attacks take advantage of vulnerabilities that allow them to eavesdrop on data transfers or communications. These vulnerabilities can be avoided with the help of developers who conduct periodic or regular audits. Security audits and vulnerability assessments ensure that security flaws are found and resolved before threat actors find and exploit them. Empower usersAnother indispensable contribution from developers is building security mechanisms right into apps or programs. Developers can provide clear warnings on potential security issues through Providing users with information about the security implications of their actions or choices is a good way to educate the public about cybersecurity. It may be a small step, but it can subliminally instill in users’ minds the importance of security practices. At the very least, it can acquaint them with the threats, risks, and attacks they usually have no idea about. Cybersecurity is no longer the sole responsibility of cybersecurity teams. With the shift-left movement becoming a necessity in recent years because of more aggressive and sophisticated attacks, developers are also playing a role in fighting cyber threats, including the lesser-known ones like MitM. More InformationMan in the middle (MITM) attack Man-in-the-Middle Attacks without Rogue AP: When WPAs Meet ICMP Redirects Understanding Website Certificates Related ArticlesFive Tips For Securing GitOps Environments Secure Coding Best Practices for 2022 To be informed about new articles on I Programmer, sign up for our weekly newsletter, subscribe to the RSS feed and follow us on Twitter, Facebook or Linkedin.
Comments
or email your comment to: comments@i-programmer.info |
|||
| Last Updated ( Monday, 12 June 2023 ) |