| GitHub and Gradle Partner To Strengthen Supply Chain Security |
| Written by Nikos Vaggalis |
| Thursday, 30 May 2024 |
|
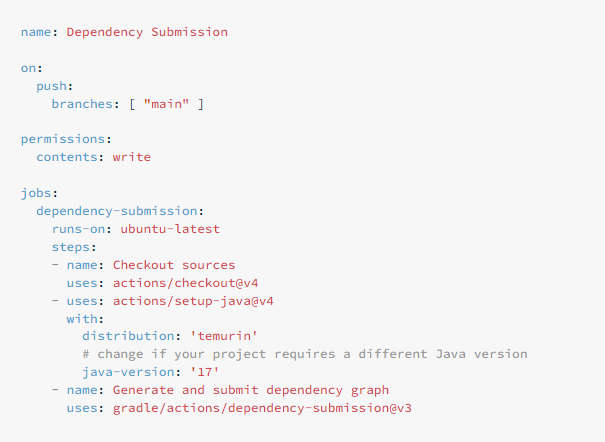
Integrating Gradle builds with Github's Actions promotes the best security practices among Gradle users. To do this there's a new official and open-source GitHub Action that generates complete and accurate information about dependencies in Gradle projects courtesy of Dependabot. Supply chain security is all the rage right now. The Linux Foundation explains it well: To build useful software we don't reinvent the wheel but we base on work already done coming bundled in the form of libraries.The problem is that even a mediocre open source project can have loads of such dependencies which themselves depend on others, forming a lengthy chain.Not a problem per se unless malicious code or security vulnerability finds its way anywhere in this chain. A way of strengthening against it is by integrating security in the software's development life cycle rather than treating it as an aftermath. To do this, GitHub which is where all the code nowadays resides, offers Dependabot which is a bot that alerts you when your repository is using a software dependency with a known vulnerability, see GitHub Dependabot Now Warns Of Vulnerabilities. Since last year a new Export SBOM functionality has been added which generates an NTIA-compliant software bills of materials (SBOMs) on demand. As detailed in Github Provides Self-Service SBOMs, Github then lets you upload your SBOMs to the Dependency Graph service, which will then scan your dependencies for known vulnerabilities in order to receive Dependabot alerts if any are present. It has also introduced a GitHub Action which bakes the SBOM generating process into the repository's CI deliverables. Since Gradle is one of the most used build tools among GitHub users, the partnership with Github has forged the new Dependency Submission Action for Gradle, an official and open-source GitHub Action that generates complete and accurate information about dependencies in Gradle projects which uploads to GitHub dependency graph. This information allows maintainers to view the dependencies of their projects in GitHub and get notified when vulnerable dependencies are detected. The issue usually is that consumers find it often difficult to map a vulnerability entry to the package versions they are using. To alleviate that and to provide complete and accurate dependency versions, the Dependency Submission Action for Gradle applies a specialized Gradle plugin which runs a small Gradle build that resolves all project dependencies. This means that the submitted dependency versions are exactly the same as those actually used by the project. So when a vulnerable dependency is detected, project admins and maintainers can be automatically notified via Dependabot alerts. To enable it for basic usage, you need a simple YAML file in .github/workflows/ directory of your repository, for example, .github/workflows/dependency-submission.yml:
sigstore-java, currently under development, is a tool for signing and verifying Java package distributions with Sigstore's keyless signing. Sigstore signing empowers software developers to securely sign software artifacts such as release files, container images and binaries. These signatures are then stored in a tamper-proof public log - for free. To make it easier to sign and publish to Maven central, the signing activity is going to be incorporated into Java's build tools Of course, there's much more to do in securing the supply chain which the latest ChainGuard "SLSA++ A Survey of Software Supply Chain Security" looks in depth by examining how the industry is adopting the best practices. For more details on that make sure to check out my article, Surveying Software Supply Chain Security. More InformationThe dependency-submission action GitHub Actions for Gradle builds Related ArticlesGitHub Dependabot Now Warns Of Vulnerabilities Github Provides Self-Service SBOMs Surveying Software Supply Chain Security Insights Into Software Supply Chain Security
To be informed about new articles on I Programmer, sign up for our weekly newsletter, subscribe to the RSS feed and follow us on Twitter, Facebook or Linkedin.
Comments
or email your comment to: comments@i-programmer.info |