| Extent Of Buggy and Risky Open Source Code Revealed |
| Written by Janet Swift | |||
| Wednesday, 08 March 2023 | |||
|
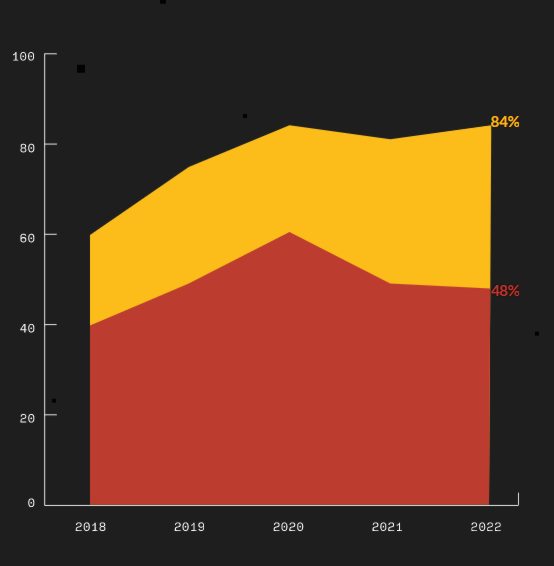
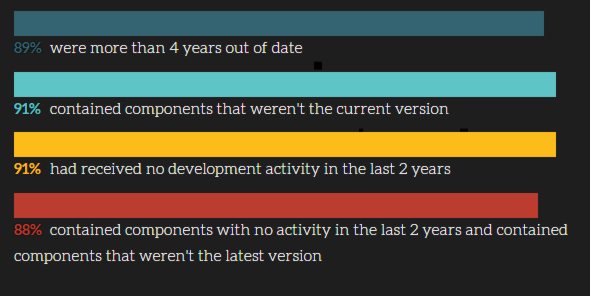
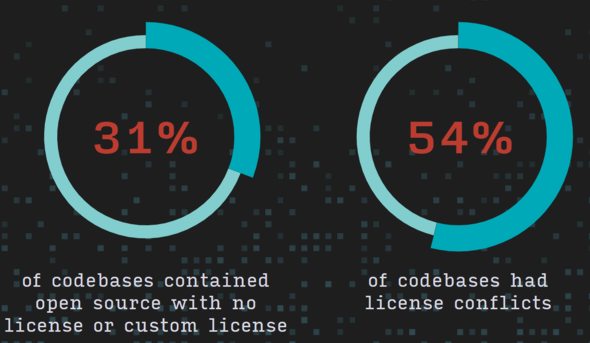
Almost all software contains open source code and the vast majority of codebases contain at least one know open source vulnerability. In addition codebases are made of of multiple components, many of which are outdated. Licence issues are also prevalent. These findings come from the Cybersecurity Research Centre at application security company, Synopsys in the 8th edition of its "Open Source Security and Risk Analysis” (OSSRA) report. The report examines the results of more than 1,700 audits of commercial codebases performed by the Black Duck® Audit Services team, primarily for merger and acquisition transactions. The first finding is that 96% of scanned codebases contained open source and that 76% of code in codebases was open source. Commenting on the way in which open source serves as the foundation for the vast majority of commercial codebases the report says: In fact, it’s so intertwined in modern development that code owners often don’t know the open source components in their own software. The codebases scanned came from 17 industry sector and there was some variation in the inclusion of open source by industry with Aerospace, aviation, automotive, transportation, logistics; EdTech; and Internet of Things being the three that had open source in 100% of their audited codebases. In the remaining sectors, over 92% of the codebases contained open source. The report charts the presence of security vulnerabilities over the past 4 years, revealing that in 2022 84% of codebases contained at least one vulnerability and 48% of codebases contained high-risk vulnerabilities: Further to this it states: The overall percentage of codebases containing security vulnerabilities remains troublingly high. After a year of modest progress, there was another slight uptick (4%) in vulnerabilities during 2022. On a more positive note it points out: While overall vulnerabilities were slightly up, the percentage of codebases with high-risk vulnerabilities was down 2% from last year, to 48%. Also promising was fewer instances of Log4J, which was found in 11% of audited Java codebases this year, down from 15%. While an improvement, this points to a larger trend of organizations failing to implement patches. Moving on from specific bugs to operational risk it reported that a high number of codebases contained outdated or moribund components: Another worrying finding is that 15% of codebases used more than 10 versions of a component. Expanding on this problem the report states> The average number of open source components in a given application this year was 595. When monitoring for security vulnerabilities and performing security maintenance activities, what might be practical for a small number of components becomes overwhelming and virtually impossible at this scale. The other problem explored in the report was the use of unlicensed code, or situations in which there were conflicts between licences.
So what is the solution to what seems to be a much bigger problem that we might have imagined. Accord to the report, it is to manage code usage with an SBOM, a Software Bill of Materials. To quote from the report: In the fight against software supply chain attacks, an SBOM should be your weapon of choice. The concept of an SBOM derives from manufacturing, where the classic Bill of Materials is an inventory detailing all the items included in a product. When a defective part is discovered, the manufacturer knows which of its products is affected and can begin the process of repair or replacement. Similarly, maintaining an accurate,up-to-date SBOM that inventories open source components is necessary
More InformationSynopsys 2023 Open Source Security and Risk Analysis Report Related ArticlesSecurity Flaws The Effects of Time and Language Professional Open Source Software Management Track Open Source Vulnerabilities With Google's OSV Database Ever Increasing Need For Secure Programming To be informed about new articles on I Programmer, sign up for our weekly newsletter, subscribe to the RSS feed and follow us on Twitter, Facebook or Linkedin.
Comments
or email your comment to: comments@i-programmer.info |
|||
| Last Updated ( Wednesday, 08 March 2023 ) |