| Ransom32- Even JavaScript Can Implement Ransomware |
| Written by Nikos Vaggalis | |||
| Monday, 11 January 2016 | |||
|
Despite JavaScript living inside the browser's protected and sandboxed environment, thus restricted on what it can or not do on the user's machine, it is still possible, just by innocently browsing the web, for those restrictions to be bypassed upon infection with 'drive-by download' malware.
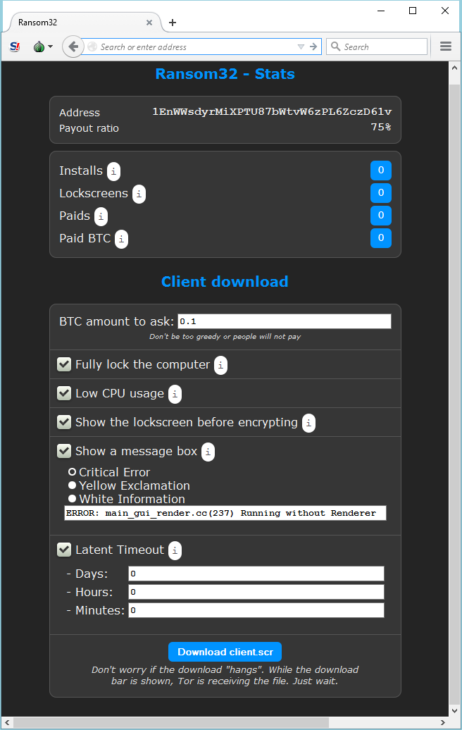
A sandboxed environment means that the JavaScript that runs in the browser can only perform Web-related actions and not actions like reading your “My Documents” folder, since it's not allowed access to the filesystem or to any other processes. The second imposed restriction on the JavaScript scripts running on the user's browser is the Same Origin Policy which disallows third party websites of getting hold of the information belonging to another site such as the sessions and cookies active when logging into your financial institution's web site. Both of these countermeasures can be beaten however, by delivering malicious JavaScript code through the browser. That code does also fall into the same restrictions imposed by the JavaScript security model but the difference is that they are able to exploit vulnerabilities and bugs in the end user's browser or in the third party plugins loaded in the user's browser. That is also the reason that all major browsers have started deprecating all third party plugins as "old plugins increase your risk for attack by malware, viruses, and other security threats",the most infamous cases being that of Adobe Flash and Java plugins, as Google and Mozilla pull the plug on Adobe Flash details Drive by downloads need to download a binary file to the user's machine either through tricking the user into download it or without user intervention. This typically happens by merely visiting a 'bad' link (therefore the 'drive by' characteristic), or being redirected from a legitimate website to a malicious one by exploiting vulnerabilities, most often those of cross-site scripting (XSS), hidden in the code of the legitimate site. XSS bugs are very difficult to identify and need either elaborate manual code revisioning or an automated solution like the Burp Suite capable of probing for exploits. For more information check our recent article Tactical Pentesting With Burp Suite. The virus in question, named Ransom32, is spread using the same method and adds to an already large collection of ransomware at large such as the FBI ransomware. What makes this one different? The difference is that it is completely written in JavaScript using the NW.js toolkit NW.js allows writing native,fully fledged applications in JavaScript like traditional languages do,say C++, therefore breaking out of the restrictions imposed by the browser's sandbox since its presence is no more required for them to run, having to deal with the OS directly and the permissions or restrictions it imposes. The virus is clearly a product of the organized crime as it can be obtained through the dark web by paying a fee in bitcoins. After access has been granted the aspiring criminal meets a dashboard that enables him to perform various actions such as declaring the Bitcoin account where the victims' bitcoins will be collected, configuring the messages the victim will be confronted with and more
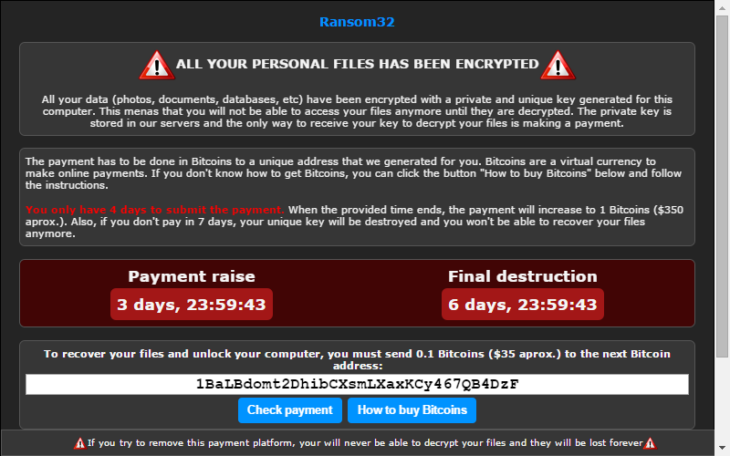
Bitcoin's property of anonymity is once more exploited for sinister purposes,such as happening in the recent Coordinated Cyber Attack on Greek Banks The malware itself is packaged into a Winrar self extracting archive that installs without the user's intervention. After getting unpacked and installed,it communicates with a control server through a Tor encrypted tunnel, and retrieves keys that will be used for encrypting many and various user files with formidable AES 128bit encryption. After the encryption is done a scary looking message is presented to the user demanding that ransom be paid within a 2-3 days interval to a Bitcoin account of the perpetrators liking, else witness all files getting destroyed!
The current form of the malware applies to Windows only but Emisoft, the researchers that identified the risk, say that it's a matter of time that it gets repackaged for use in an other operating system like Linux, as NW.js nature allows an application be written once and be deployed to many. So what can you do,how can you mitigate the risk?
More InformationMeet Ransom32: The first JavaScript ransomware Related ArticlesTactical Pentesting With Burp Suite
To be informed about new articles on I Programmer, sign up for our weekly newsletter,subscribe to the RSS feed and follow us on, Twitter, Facebook, Google+ or Linkedin.
Comments
or email your comment to: comments@i-programmer.info |
|||
| Last Updated ( Wednesday, 13 January 2016 ) |