| How Secure Is Android? Very Secure |
| Written by Alex Armstrong | |||
| Wednesday, 08 April 2015 | |||
|
In the past Android has had a poor reputation for security but this may be undeserved as a new report from Google spells out in detail. Apple has traditionally cited device security as one of its selling points. If you've been deterred from choosing Android on the grounds that you might encounter a "potentially harmful app" (PHA) Google's statistics should prove reassuring. The newly published Android Security 2014 Year in Review is based on billions of data points gathered every day during 2014 to provide a comprehensive and in-depth insight into security of the Android ecosystem. In his summary of the report's key points on the Google Online Security blog, Adrian Ludwig, Lead Engineer for Android Security,writes: Android offers an application-focused platform security model rooted in a strong application sandbox. We also use data to improve security in near real time through a combination of reliable products and trusted services, like Google Play, and Verify Apps. And, because we are an open platform, third-party research and reports help make us stronger and users safer. Ludwig highlights the following findings:
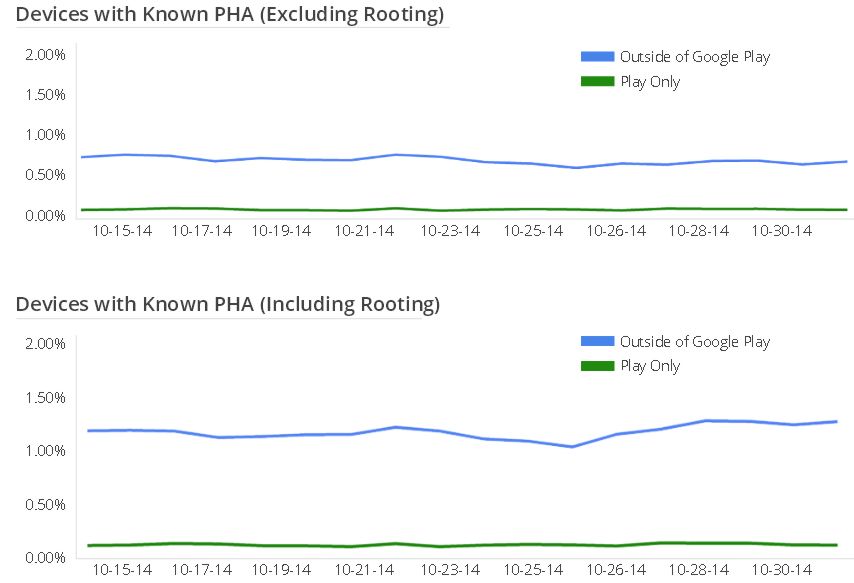
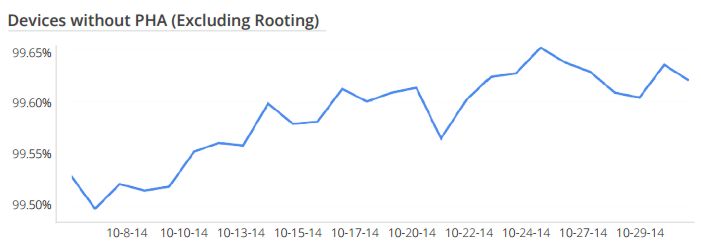
To expand on this, two types of security services are provided by Google Play for all Android users. Apps downloaded from Google Play are reviewed for potentially harmful behavior and subjected to ongoing protection. Google Play also has a service called Verify Apps that provides protection from apps outside of Google Play regardless of source of install that includes a technology code-named “Safety Net” that detects and protects against non app-based security threats such as network attacks. Google began to collect a statistic referred to as "device hygiene on October 2014. As shown in this graph during October 2014, the lowest level of device hygiene was 99.5% and the highest level was 99.65%. Thus fewer than 0.5% of devices had a PHA installed (excluding non-malicious Rooting apps).
Rooting tools are prohibited within Google Play. However, Verify Apps detects rooting applications that provide local privilege escalation installed on approximately 0.5% of devices, having been installed from sources outside of Google Play, but fewer than 1 in a million of these are characterized a "malicious".
There are marked regional variations in the prevalence of PHAs with Chinese and Russian devices having the most as this chart, for October 2014, reveals:
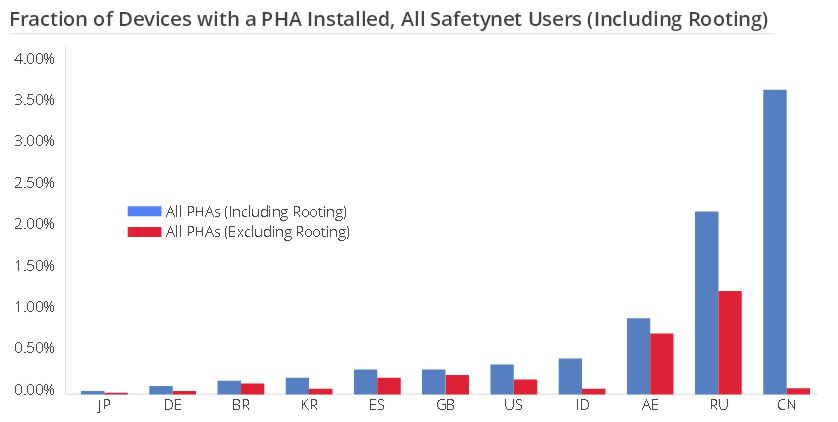
The bottom line is that worldwide the incidence of PHA's for installs outside of Google Play including rooting was only 0.5% for the second half of 2014 and fewer than 0.15% of devices that only install from Google Play had a PHA.
More InformationAndroid Security State of the Union 2014 Android Security 2014 Year in Review (pdf) Related ArticlesAndroid Security Hole More Stupid Error Than Defect Android Security Internals (book review)
To be informed about new articles on I Programmer, install the I Programmer Toolbar, subscribe to the RSS feed, follow us on, Twitter, Facebook, Google+ or Linkedin, or sign up for our weekly newsletter.
Comments
or email your comment to: comments@i-programmer.info |
|||
| Last Updated ( Thursday, 09 April 2015 ) |