| NIST Selects Lightweight Crypto For The IoT |
| Written by Mike James | |||
| Wednesday, 15 February 2023 | |||
|
Amateurs implementing cryptography are a security problem. Ergo, the IoT has a security problem. Will a more suitable cryptography suite help?
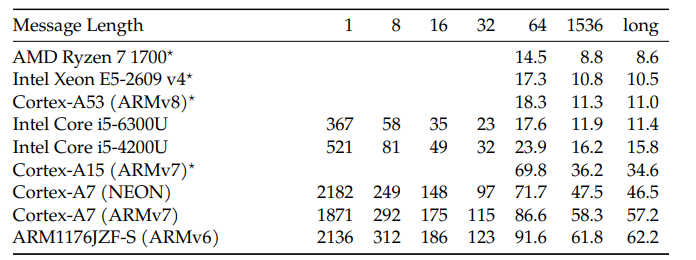
NIST, the National Institute of Standards and Technology, has been running a competition to find a good method of protecting data in small devices. Started in 2018 the competition received 57 entries and after public review this was reduced to 10 candidates. Now we have a "winner" - Ascon. Ascon was developed in 2014 by cryptographers from Graz University of Technology, Infineon Technologies, Lamarr Security Research and Radboud University and it has already won a similar competition for authenticated encryption. There are seven variations in the Ascon family and not all will necessarily make it to the final NIST IR 8454 standard. The new algorithms perform Authenticated Encryption with Associated Data AEAD and hashing. Currently the best AEAD algorithm is AES with Galois Counter Mode and the best hash is SHA-256 and both are commonly used in HTTPS/TLS connections. These are symmetric key algorithms and so is Ascon, but of course you could always arrange a key exchange using asymmetric key PKI crypto. As to efficiency: Ascon is natively defined on 64-bit words using only the bitwise Boolean functions and, xor, not, and rot (bitwise rotation). This significantly reduces the effort of implementing the algorithm on new target platforms. I can think of architectures that struggle with 64 bit operations but this is becoming increasingly rare. The performance of Ascon-128 (in cycles per byte) is given as:
The strange fact is that recent research has demonstrated that Ascon was slower and used a similar amount of memory to AES, but this was attributed to how well tuned the AES algorithm was. It also seems to have a low requirement for implementation in hardware. The announcement of the winner also points out the Ascon isn't resistant to attack by a quantum computer but this hardly seems to be an issue given the short life of most IoT data. As big a problem, when it comes to small machines, is keeping the keys private. Given that the IoT device is accessible to an attacker, storing private keys without special hardware isn't secure at all against a hardware-based attack. Will we see Ascon as part of TLS in the near future? Only after there is a standard is my guess.
More InformationNIST Selects ‘Lightweight Cryptography’ Algorithms to Protect Small Devices Analysis of Practical Application of Lightweight Cryptographic Algorithm ASCON (pdf) Related ArticlesWhat Does The NSA Think Of Cryptographers? Stick Figure Guide To AES Encryption To be informed about new articles on I Programmer, sign up for our weekly newsletter, subscribe to the RSS feed and follow us on Twitter, Facebook or Linkedin.
Comments
or email your comment to: comments@i-programmer.info
|
|||
| Last Updated ( Wednesday, 15 February 2023 ) |

 The IoT has a particular problem with cryptography in that the processors and memory available are insufficient for dealing with the standard algorithms in an acceptable way. For example, using the Raspberry Pi Pico, which is more powerful than the average IoT device, it can take five seconds or more to establish an HTTPS/TLS connection using a strong key exchange algorithm.
The IoT has a particular problem with cryptography in that the processors and memory available are insufficient for dealing with the standard algorithms in an acceptable way. For example, using the Raspberry Pi Pico, which is more powerful than the average IoT device, it can take five seconds or more to establish an HTTPS/TLS connection using a strong key exchange algorithm.