| Largest Ever Pwn2Own Contest |
| Written by Sue Gee |
| Friday, 16 December 2022 |
|
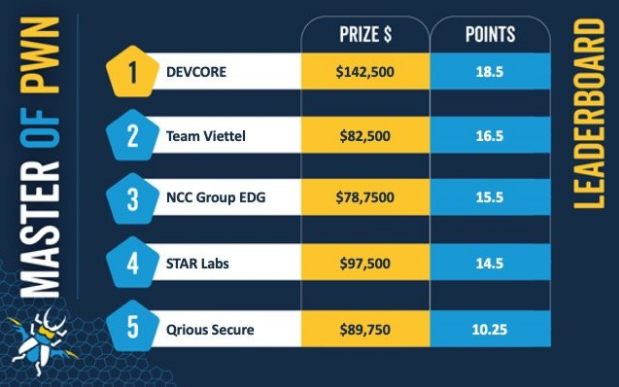
The recent Pwn2Own event held at ZDI's offices in Toronto was extended to 4 days to accommodate 26 contestants and teams attempting to exploit 66 targets across multiple categories. By the end there had been bounty payouts totalling $989,750 USD for 63 new bugs. This contest is now wholly owned by Trend Micro and wasn't held in conjunction with a conference. The organizers still wanted contestants to attend in person and offered $3,000 in travel expenses for teams to participate in Toronto. There had been 85 entries but shortly before the contest NETGEAR announced some patches to fix bugs that had been scheduled to be demonstrated during the contest and TP-Link and Sonos also released updates. As a consequence, many contestants withdrew their entries. In a blog post, ZDI's Brian Gorenc commented: One of our goals with Pwn2Own is to incentivize companies to improve the security of their devices and services, so it’s great to see improvements happen – whether they are a direct result of Pwn2Own entries or pre-emptive patches that stop Pwn2Own entries. It also highlights the skill and ingenuity of the researchers participating in the contest as many had quickly bypassed the patch and re-submitted entries. By the time we started the contest, we had ramped back up to 66 entries scheduled for four days. This was the 10th anniversary of ZDI's consumer-focused version of the contest, formerly known as Mobile Pwn2Own. It now focuses on devices typically found in homes and home offices and a new feature of this edition of the contest was a "real world scenario" dubbed SOHO (as in Small Office/Home Office) Smashup. This challenge is modelled on how a threat actor would exploit a home office in that contestants were ask to nominate a router to hack via the WAN interface. They then had to pivot into the LAN to their choice of second target, one of the other devices in the contest. Compromise both to win $100,000 and 10 Master of Pwn points but fail at either and come away empty handed. In the event eight teams of researchers decided to back themselves to go for the superbounties available through Smashups and six of them succeeded in getting in through the router and then onto a printer. Only one of the teams that tried for a Smashup aimed at anything other than a printer once inside. The Qrious Security duo from Vietnam had a go at the Western Digital NAS via a NETGEAR router, but didn’t get all the way to their target within the 30 minute limit imposed by the rules of the competition. Here's the leaderboard as it stood at the end of the contest and the Naked Security blog by Sophos disclosed what is known about the corporate teams in the top three positions: 1. DEVCORE works for a Taiwanese red-teaming and cybersecurity company whose official website includes staff known only by mysterious names such as Angelboy, CB and Meh. 2. NCC Group EDG comes from the dedicated exploit development group (EDG) of a global cybersecurity consultancy originally spun off in 1999 from the UK government’s National Computer Centre. 3. Viettel Security is the cybersecurity group of Vietnam’s state-owned telecommunications company, the country’s largest. The final payout might have been greater but the most lucrative targets were not even attempted. These were the phones from Apple and Google, worth $200,000 each (plus a $50,000 bonus for kernel-level access), and the home hubs from Meta, Amazon and Google the speakers from Apple, Amazon and Google worth $60,000 each. The only $60,000-bounty that paid out was the one offered by Sonos, whose speaker was successfully attacked by three different teams. One possible reason for the big-name phones and speakers not being tested were that there are alternative bug-buying services that claim to offer much higher bounties that Trend Micro making any bugs that could be discovered are more valuable elsewhere. These days security research is a serious business undertaken by highly professional teams.
More InformationRelated ArticlesMicrosoft Edge Falls Victim At Pwn2Own Get Ready for Expanded Pwn2Own 2017 Largest Payout Ever At Pwn2Own 2015 To be informed about new articles on I Programmer, sign up for our weekly newsletter, subscribe to the RSS feed and follow us on Twitter, Facebook or Linkedin.
Comments
or email your comment to: comments@i-programmer.info |
| Last Updated ( Friday, 16 December 2022 ) |