| Sigstore Reaches General Availability |
| Written by Nikos Vaggalis | |||
| Tuesday, 25 October 2022 | |||
|
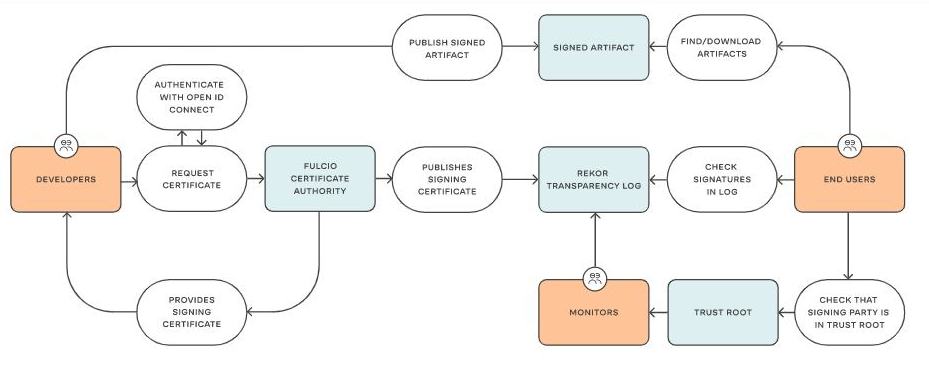
Sigstore has announced the General Availability of its free software signing service giving open source communities access to production-grade stable services for artifact signing and verification. The GA was announced today at SigstoreCon and finally removes the last barrier standing before the widespread adoption of its supply chain security solution. The Kubernetes and Python communities have already adopted Sigstore’s wax seal of authenticity by signing their production releases with Sigstore, with npm looking to follow soon. According to Zach Steindler, program manager for npm integration: “Sigstore will power a new security capability in the npm ecosystem - a reliable way to connect a package back to its source code and build instructions. The GA means we can rely on it in production, which in turn gives our users more confidence that npm packages contain what they claim. This couldn't be more timely, as everyone is looking to improve their software supply chain security. ” GA status makes it possible for every open source project out there and not just the elite to come onboard too, signaling the stability and reliability necessary for adoption; Sigstore has your backs. The service will be free to use for all developers and software providers, with the sigstore code and operation tooling developed by the sigstore community. As a refresher, the Sigstore ecosystem consists of:
This ecosystem empowers software developers to securely sign software artifacts such as release files, container images and binaries, whose signing materials are then stored in the tamper-proof public log. I have recently looked at yet another such tool, Gitsign: Since everybody is on Git, what better way of starting with signing the initial artifacts of the supply chain, the commits? While Sigstore had released tools for signing containers and binaries, there was nothing for signing git commits. This is about to change with Gitsign, which allows you to sign your commits in a keyless fashion by using your GitHub / OIDC identity. Not only does this relieve you of the burden of managing the keys yourself, it also deal with the issue of those keys many times ending up being written inside the source of the repo itself, in effect canceling out the signing process. But container security is not left out of the picture too, with Chainguard, the co-creator of Sigstore, launching Wolfi, a community Linux (un)distribution that is built with the default security measures necessary for securing the software supply chain: The push for software supply chain integrity and transparency has left organizations struggling to build in software security measures like signatures, provenance, and SBOMs to legacy systems and existing Linux distributions. To that end, Sigstore is good but requires manual labor. There must be a better way of utilizing its facilities. And what better than package all the work in an immutable container? Chainguard’s new Linux (un)distribution and build toolchain, Wolfi, is doing exactly that. It produces container images that meet the requirements of the secure software supply chain; that is images already provided with signing and sensible defaults. But the tools mean nothing without documentation and training in applying them to real use cases. For that reason the Linux Foundation, in partnership with Chainguard, has launched a new course to educate developers in : Chapter 1. Introducing Sigstore Chapter 2. Cosign: Container Signing, Verification, and Storage in an OCI Registry Chapter 3. Fulcio: A New Kind of Root Certificate Authority For Code Signing Chapter 4. Rekor: Software Supply Chain Transparency Log Chapter 5. Sigstore: Using the Tools and Getting Involved with the Community With all that effort being put as well as the recent service's GA, consumers of OSS should start feeling much much safer. . . More InformationRelated ArticlesProtect The Software Supply Chain With Gitsign Wolfi Linux (Un)Distribution Secures The Software Supply Chain Securing Your Software Supply Chain With This Free Course
To be informed about new articles on I Programmer, sign up for our weekly newsletter, subscribe to the RSS feed and follow us on Twitter, Facebook or Linkedin.
Comments
or email your comment to: comments@i-programmer.info |