| JavaScript Prototype Vulnerabilities |
| Written by Ian Elliot | |||
| Wednesday, 23 March 2022 | |||
|
The first large scale investigation of the prevalence of JavaScript prototype pollution reveals that more than 2,700 of websites, including ten among the top 1,000 had flaws that could expose them to exploitable vulnerabilities. Discovered in 2018, prototype pollution is a relatively new type of JavaScript vulnerability and is due to a JavaScript feature, called prototype chain, which allows a property lookup not only under the current object but also through a chain of prototypical objects. This is how JavaScript implements inheritance. According to Yinzhi Cao, Assistant Professor of Computer Science in the Johns Hopkins Whiting School of Engineering who devised the ProbTheProto framework, prototype pollution empowers an adversary to inject or modify a property under a prototypical object, e.g. Object.prototype, thus affecting the normal execution (e.g., control- and data-flows) of a vulnerable program. Explaining the problem informaly to Catherine Graham on the John Hopkins University blog. Cao said: In Javascript, an object is a collection of related data or functionality; for example, a user account object may contain such data as usernames, passwords, and e-mail addresses. Once an attacker makes a change to an object prototype, it will affect how the object works throughout the entire application and opens the door for more serious vulnerabilities. commenting "Only recently have researchers started looking closely at prototype pollution and realizing it's a matter of great concern. Many in the developer community may not be aware that prototype pollution vulnerabilities can have severe consequences." Cao's ProbeTheProto framework is intended to identify and alert vulnerable websites and consists of two parts: dynamic taint analysis that tracks so-called joint taint flows connecting property lookups and assignments, and input/exploit generation that guides joint taint flows into final sinks related to further consequences. Further, ProbeTheProto looks into whether a prototypical object is controllable, whether and what properties can be manipulated, and whether the injected value leads to further consequences. it does this by tracking adversary-controlled inputs into vulnerable property lookups, such as obj[prop], via dynamic taint analysis to detect prototype pollution vulnerabilities, and then guiding object lookups in propagating taints to a consequence-related final sink like innerHTML. With PhD students, Zifeng Kang, Song Li, Cao implemented a prototype of ProbeTheProto and evaluated it on the top one million websites as ranked by Tranco. Their results identified 2,738 websites that are vulnerable to 2,917 zero-day, exploitable prototype pollution vulnerabilities.
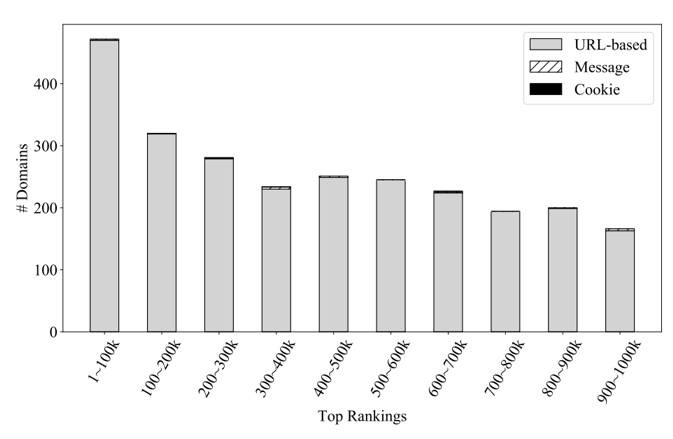
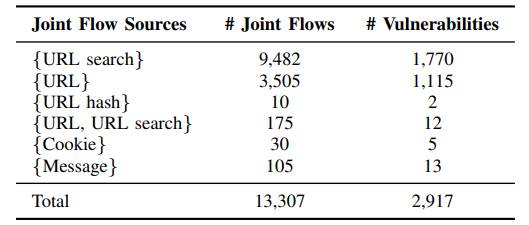
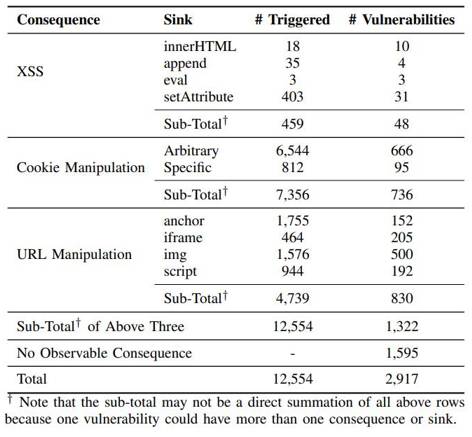
The distribution of vulnerabilities shows that the more popular websites were more likely to be exposed to prototype pollution. In fact, 10 among the top 1,000 websites, including CNET.com, weebly.com and mckinsey.com were among those identified as were 63 sites ranked between 1,000 and 10,000. Looking at the breakdown of zero day prototype pollution among the one million websites by joint flow sources, URL search (location.search) is by far the most numerous, followed by URL (location). A small number of vulnerabilities were introduced by messages and even fewer by cookies. The breakdown of vulnerabilities by consequences shows the number of times that the sink is being triggered: It shows that cookie and URL manipulations are much more popular than XSS. A final sink for one vulnerability may be triggered multiple times because it is often embedded in a for loop or being invoked in multiple function calls. In all, 1322 vulnerabiliities are further vulnerable to other attacks - 48 lead to XSS, 736 to cookie manipulation and 830 to URL manipulation. The other 1595 had no observable consequences. By the time the paper, which is to be presented at the Network and Distributed Systems Security (NDSS) Symposium 2022 being held in San Diego, California, USA at the end of April, was drafted, 185 websites had fixed the reported vulnerabilities, six others had confirmed but not yet fixed the flaws, and two had been patched with their own fix but are still vulnerable.
More InformationProbe the Proto: Measuring Client-Side Prototype Pollution Vulnerabilities of One Million Real-world Websites (pdf) Related ArticlesJust JavaScript - The Prototype Mechanism Just JavaScript - ES2015 Class Javascript Jems - The Prototype To be informed about new articles on I Programmer, sign up for our weekly newsletter, subscribe to the RSS feed and follow us on Twitter, Facebook or Linkedin.
Comments
or email your comment to: comments@i-programmer.info |
|||
| Last Updated ( Wednesday, 23 March 2022 ) |