| TPM Security Easy To Defeat |
| Written by Harry Fairhead |
| Wednesday, 18 August 2021 |
|
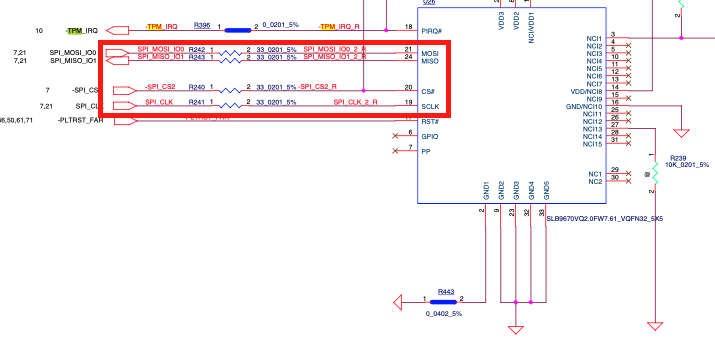
The headline says it all, but not in sufficient depth for you to understand exactly what the situation is. There is a hardware hack that means that you can compromise a machine that has been set up in a particular way. This is important, but it's not a TPM killer. What is surprising is how simple the hack is considering that TPM is the state of the art security hardware. The TPM - Trusted Platform Module - is present in most modern machines, but it is often switched off. Microsoft plans to make it a requirement for Windows 11 and various Windows features such as BitLocker are significantly easier to use with it switched on. Linux also makes use of it, but it is less of a "selling point" as few try to actually sell Linux. What all this means is that secure isn't so secure and it is a lesson in how things can go very wrong. I'm not a security guy. In fact, I find most things about security to be fairly boring and usually a nuisance that gets in the way of getting a job done. This isn't to say that I think security is irrelevant, it's just that I consider it someone else's problem. However, the TPM is hardware and I'm interested in hardware so to my surprise I discovered that this particular attack is very easy if you know some hardware techniques. The attack has been known for a while, but it resurfaced in a practical form when the Dolos Group was given a laptop to use as a test of security. In the blog describing the events that unfolded the laptop is described and seems well locked down, apart from the fact that the encrypted BitLocker disk is secured using the TPM. This should mean maximum security because the hardware is designed to be secure, as the researhers readily admit. But then they notice something. The TPM chip is connected to the rest of the machine via the SPI bus and with no encyrption. A circuit diagram of the laptop helped but wasn't essential.
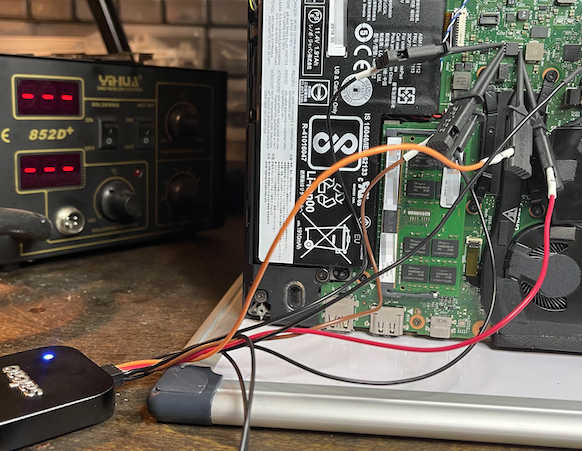
Once you know that the encryption key is sent over the SPI bus in plain text your only real problem is making a physical connection to the bus, which in these days of surface mount components isn't as easy as it used to be. Eventually the researchers found an SPI connection to a larger chip with reasonable sized pins that allowed them to attatch a logic analyzer to the bus - a fairly cheap instrument that most hardware guys have. This allows you to watch the data on the SPI bus and with the help of a software protocol analyzer you can simply read the data. This could then be fed to a BitLocker toolkit program that extracts the key without any manual input. Notice that the key extractor is very simple in that the key is in plain text and can simply be read if you know where it is in the data stream.
Once they had the key and an image of the drive, decryption was simple and from this point everything else is much easier. The researchers used the data on the disk to break into the corporate network, but this really isn't part of the story in that once you have access to the drive you can take your time and use the data in creative ways. This is refered to as an "evil maid" attack because it is supposed that if you left your laptop in a hotel room then a member of the room servicing staff have enough time to perform the attack. What is really intersting is that this is another example of how sophisticated security is useless if it has a weak link. The researchers say: "Getting around the TPM in this manner is akin to ignoring Fort Knox and focusing on the not-so-armored car coming out of it." I would say that is more like Fort Knox loading bullion into the back of a 4x4 and sending it out into the wilds and just hoping it doesn't meet anyone. The solution of course is to use encryption on the SPI bus, but that is going to be one of those security concerns that I personally hope to avoid by getting someone else to do the job. In the mean time it makes Microsoft's insistence on hardware-based security look a little less convincing. More InformationFrom Stolen Laptop To Inside The Company Network Defeating Microsoft’s Trusted Platform Module Related ArticlesMicrosoft Gives Devs Option of Keeping 100% Revenue To be informed about new articles on I Programmer, sign up for our weekly newsletter, subscribe to the RSS feed and follow us on Twitter, Facebook or Linkedin.
Comments
or email your comment to: comments@i-programmer.info
|
| Last Updated ( Wednesday, 18 August 2021 ) |