| Introduction to OAuth 2.0 and OpenID Connect |
| Written by Nikos Vaggalis | |||
| Thursday, 17 September 2020 | |||
|
Getting familiar with OpenID and OAuth is really difficult.There are dozens of specifications to go through, and to make things even worse the two protocols involve different terminology. To help out, Pragmatic Web Security offers a free and outstanding course on OAuth and OIDC 101. This is a fully fledged course with videos, texts, demo scenarios, assignments and assessments aiming to demystify both OAuth and OIDC at their core and their interconnection. It relies on the cloud-based Auth0 identity provider to run OAuth 2.0 and OpenID Connect flows because setting up an Auth0 tenant is straightforward and free. Of course, note that the use of Auth0 should not be considered as an endorsement. As to the material itself, it is broken down into six chapters:
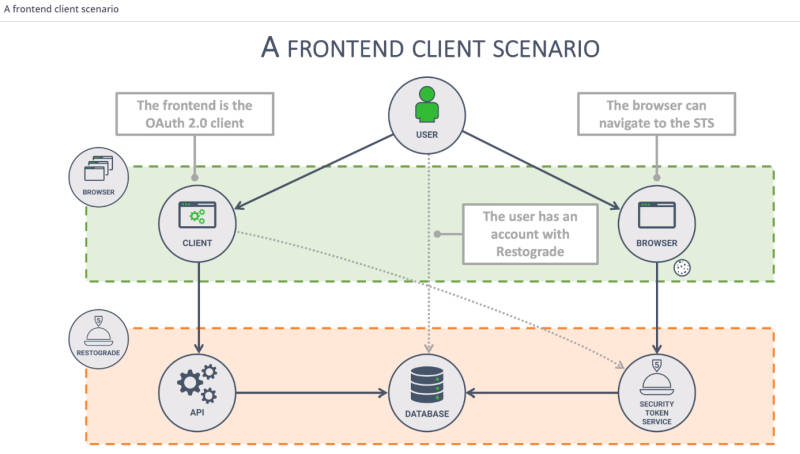
The use case scenario that runs throughout the course, is that of Restograde, a restaurant review application which allows users to leave reviews about their favorite restaurants. It's no more than a simple frontend application that connects to a backend API which in turn connects to a database behind the scenes. So far so good, and there's no need for complex authorization schemes like OAuth. But a need emerged for third party applications to be able to connect to Restograde's API. This involves another app, called Virtualfoodie, which has similar functionality to Restograde in that it allows users to explore and rate restaurants. It now wants to integrate Restograde's users' data to provide a richer experience to its own users.
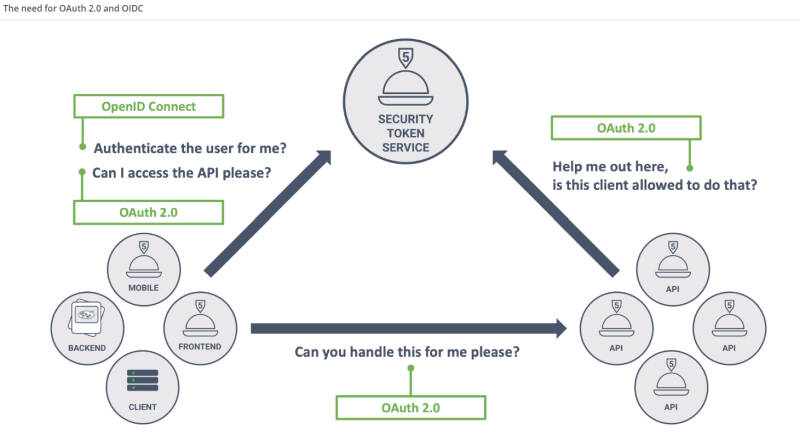
Thus Virtualfoodie needs to contact Restograde's API and for that it has to authorize - something that can be done with OAuth. In addition, The key distinction here is authentication vs authorization. The introductory chapter does a great job of putting things into perspective by clearly differentiating between OAuth's scope and use cases. The next chapters go behind the scenes of the OAuth flows. We find out how easy it is to implement a custom Security Token Service on the Auth platform, register a backend client and enable Single Sign-On scenarios through OpenID, offloading the authentication to centralized providers. After tackling how server-side applications/backend APIs connect under the OAuth flow, the class deals with the native and mobile client side of the flow, which as is demonstrated is not as secure as in the case of server-side applications. Then we move on to the frontend clients and SPAs (Singler Page Applications) which come with their own challenges.The original OAuth 2.0 specification defines four distinct OAuth 2.0 flows:
The traditional web clients build with HTML and jQuery still use the Implicit flow, which is however considered deprecated, while the newer counterparts of SPAs follow the Authorization Code flow with PKCE. Nowadays the first and the last flows are the ones still relevant. Looking into those Additional flows, and after a brief summary, the class is concluded.
To sum it up, this is a well planned and executed course. While "Introduction to OAuth2.0 and OpenID Connect" is free, the instructor, Dr. Philippe De Ryck, also offers the more advanced "Mastering OAuth 2.0 and OpenID Connect" as a paid follow-on. If you are looking to delve deep into the topic, because of your job or other requirements, I would certainly recommend it, judging from the good experience of its free counterpart. More InformationIntroduction to OAuth2.0 and OpenID Connect Related ArticlesHacksplaining - Learn Through Hacking To be informed about new articles on I Programmer, sign up for our weekly newsletter, subscribe to the RSS feed and follow us on Twitter, Facebook or Linkedin.
Comments
or email your comment to: comments@i-programmer.info |
|||
| Last Updated ( Thursday, 17 September 2020 ) |