| Firefox Raises Bug Bounty Payouts |
| Written by Alex Armstrong | |||
| Tuesday, 28 April 2020 | |||
|
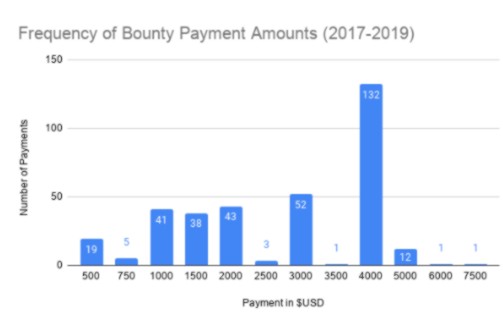
Mozilla has updated its bug bounty policy to make it more appealing to security researchers. It has also launched a new website for security researchers, and Firefox bug bounty participants. In his inaugural post to the new Attack & Defense blog Tom Ritter takes the opportunity to review the recent performance of the Firefox bug bounty program, which he notes began in 2004. Between 2017-2019, Mozilla paid out $965,750 to researchers across 348 bugs, making the average payout $2,775 – but as the graph shows the most common payout was $4,000: He also mentions that Mozilla added a new static analysis bounty to its Client Bug Bounty Program towards the end of 2019 in an attempt to encourage the community to use CodeQL tools for static analysis work that identifies present or historical flaws in Firefox. With regard to latest updates to the bug bounty policy and payouts, they are designed to reflect the more hardened security stance Mozilla adopted after moving to a multi-process, sandboxed architecture. Ritter writes: Firstly, we’re amending our current policy to be more friendly and allowing duplicate submissions. Presently, we have a ‘first reporter wins’ policy, which can be very frustrating if you are fuzzing our Nightly builds (which we encourage you to do!) and you find and report a bug mere hours after another reporter. From now on, we will split the bounty between all duplicates submitted within 72 hours of the first report; with prorated amounts for higher quality reports. We hope this will encourage more people to fuzz our Nightly ASAN builds. Increased payouts should also provide security researchers with an incentive to become involved. Sandbox escapes and related bugs will be now eligible for a baseline $8,000, with a high quality report up to $10,000. Additionally, proxy bypass bugs are eligible for a baseline of $3,000, with a high quality report up to $5,000. Pointing out that most payouts made by Mozilla are above the baseline, Ritter explains: a bounty amount is not determined based on your initial submission. but rather on the outcome of the discussion with developers. So improving test cases post-submission, figuring out if an engineer’s speculation is founded or not, or other assistance that helps resolve the issue will increase your bounty payout. The new website will also host guides on testing different parts of Firefox and two such articles by Frederik Braun, Help Test Firefox’s built-in HTML Sanitizer to protect against UXSS bugs and Remote Code Execution in Firefox beyond memory corruptions have already been reposted to it. More InformationMozilla's Attack & Defense blog Firefox’s Bug Bounty in 2019 and into the Future Mozilla Client Bug Bounty Program Related ArticlesGitHub Security Bug Bounty Milestones Over $21 Million In Google Bug Bounty Power Cycle Your Boeing 787 To Keep It Flying To be informed about new articles on I Programmer, sign up for our weekly newsletter, subscribe to the RSS feed and follow us on Twitter, Facebook or Linkedin.
|
|||
| Last Updated ( Tuesday, 28 April 2020 ) |