| Tactical Pentesting With Burp Suite |
| Written by Nikos Vaggalis | |||
| Monday, 30 November 2015 | |||
Page 2 of 2
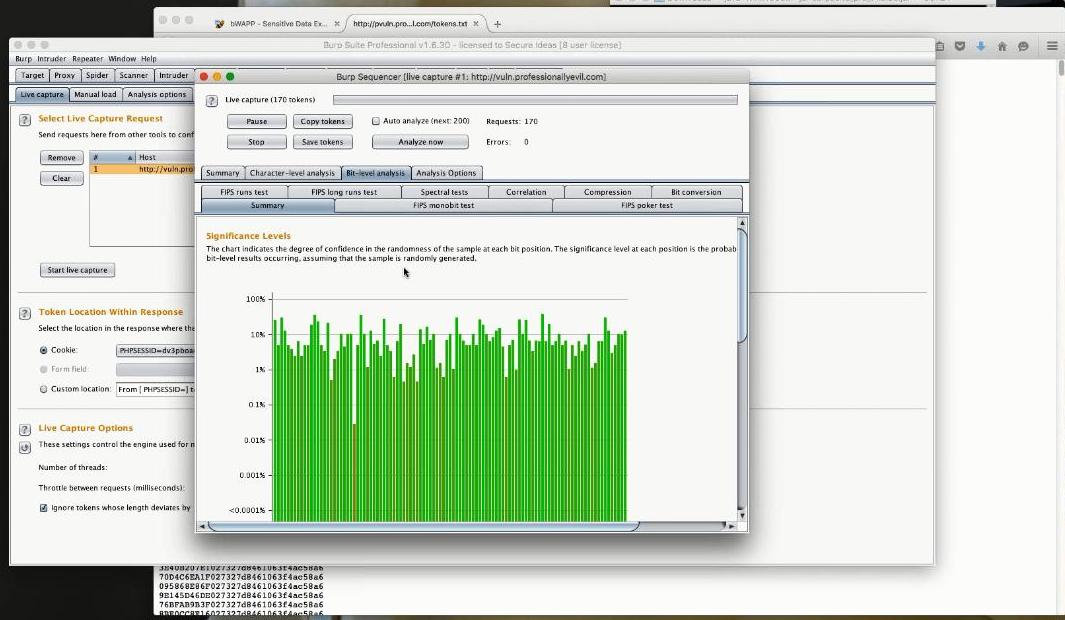
The SequencerThe Sequencer was next. This tool checks for randomness and is able to give a definitive answer to the crucial question on all developers' lips - "are the tokens we are generating random enough?".
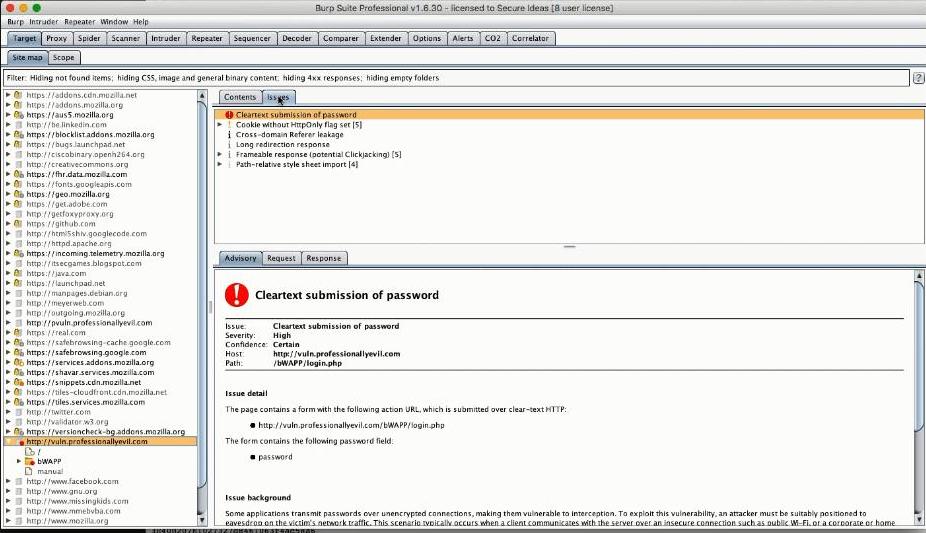
The ScannerNext in line was the Scanner, split into active and passive, used for automatically finding flaws in URL parameters, HTTP headers, Cookie parameters and so on. These scanners are in the Pro version of Burp whereas the Free version does not include them. Some hidden configuration options were exposed, which had they gone unnoticed could have a detrimental effect on overall performance. For example it's a well kept secret that the Active scanner will truncate payload positions by default, unless tweaked. After the scan is completed you are presented with a list of issues found. In this instance there were several flaws identified such as Cleartext submission of passwords; Cookies without HttpOnly flags; potential Clickjacking etc. Clicking on any issue will bring up detailed and background information and reveal the relevant HTTP request-response cycle.
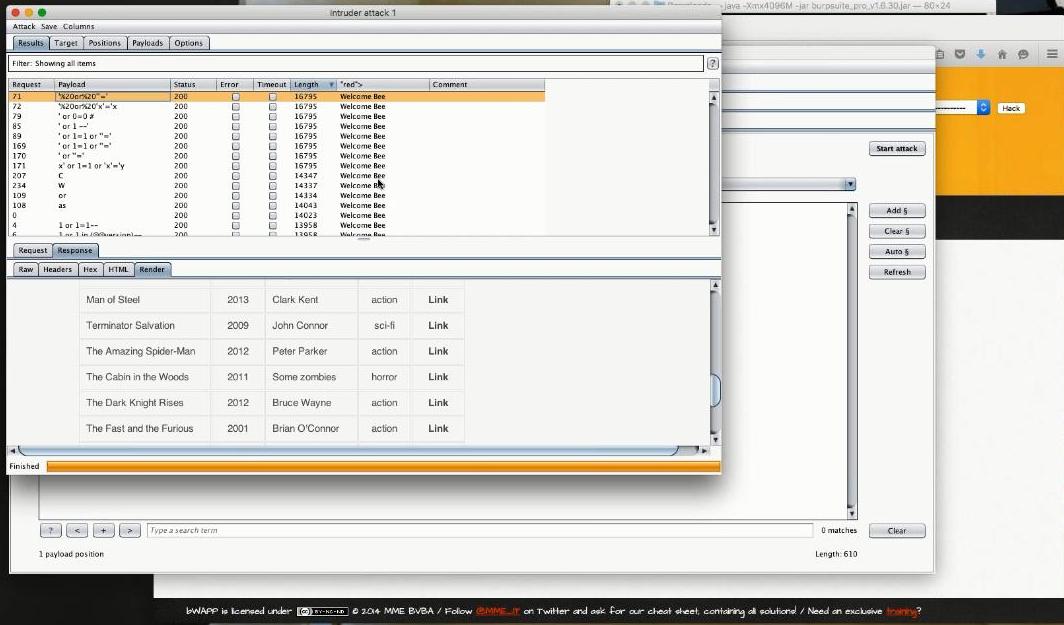
What is very interesting is that the Scanner can also identify clientside flaws through its Static Code Analysis feature. It does so by checking for hidden flaws like DOM XSS in the Javascript returned to the client, flaws that could be triggered within the browser without having to interact with the server again. The IntruderThen we get fuzzy with the Intruder, the fuzzing tool that takes multiple payloads and carries out the actual attacks. The recommended workflow is to forward the web server's captured response to the Intruder, which will automatically (remember the manual nature of the Repeater?) identify the payload positions and mark them within § symbols. The markings at those positions are then replaced with predefined inputs of your choosing, depending on the preferred attack vector (SQL injection,Reflected or Stored XSS, etc). The preferred attack vector in this instance was to inject SQL payloads, fed to the database through HTML form parameters, against a movie lookup web page, with the scope of retrieving all the movies in the database. Not very interesting you might say, but imagine that the movies were sensitive data like bank accounts instead, their retrieval being unauthorized.
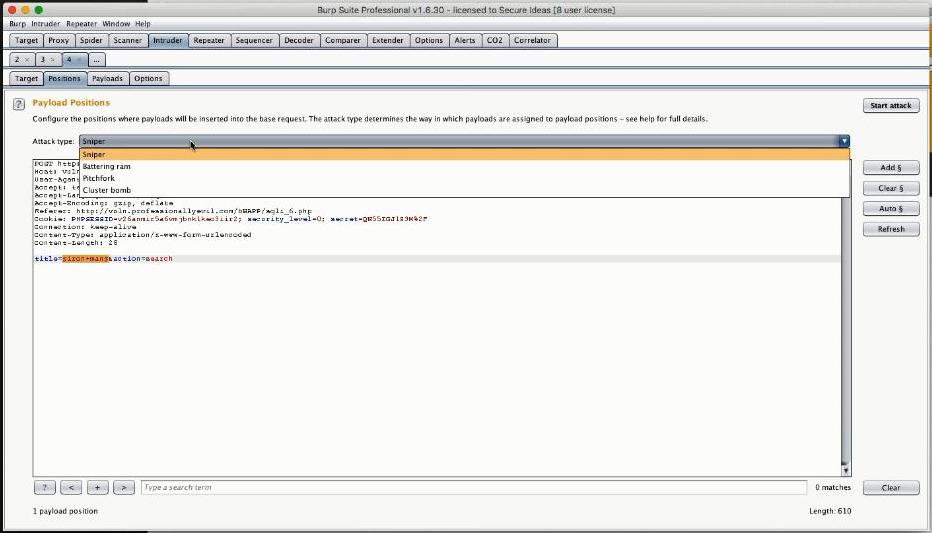
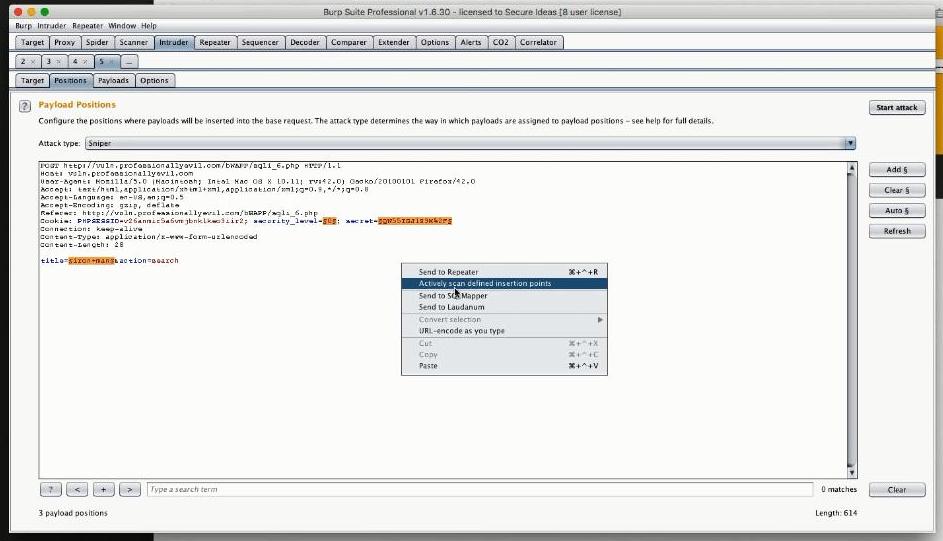
Instead of letting the Intruder use the payload positions which it had automatically identified, the instructors cleared them up and picked a subset of them manually. So they highlighted the payload position: title=iron+man&action=search and enclosed it by § by clicking Add §, resulting in: title=§iron+man§&action=search
So after Sniper was chosen, we had to navigate to the Payloads screen where we selected what type of Payload we were going to use. There were many available such as the Simple List, an ideal choice for use with the fuzzydb database of attack patterns); Brute forcer, Bit flipper, ECB block shuffler, Illegal Unicode and so on. On this occasion we went with Simple List and subsequently selected the kind of sub-list (that contains the actual payload tokens) we would like to feed into Intruder. For this example the Fuzzing SQL injection list was an obvious candidate. Sample tokens contained in the fuzzing list were : ' or 1=1-- Then we just had to click Start Attack to launch a fire and forget operation. A crucial observation at this point made by the instructors, is that the Intruder runs much slower in the free version, an artificially induced limitation. Using the Intruder with the ScannerA great trick shown was the way you can relate the Intruder to the Scanner. This works out by sending the payload positions identified by the Intruder to the Scanner, which in essence tells the Scanner to base its work on the Intruder's findings/payload positions and not on the Scanner's automatically identified ones.
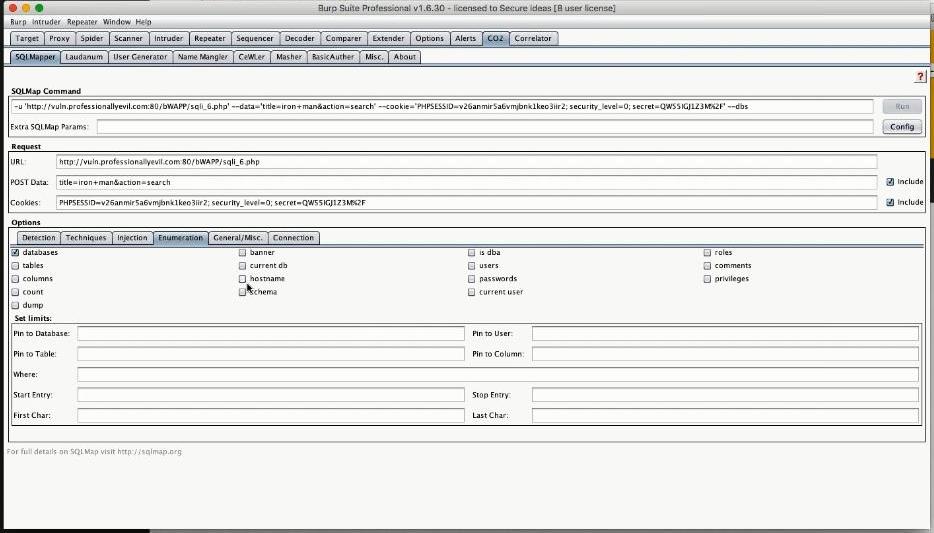
It was unclear what kind of actual payloads/test input data the Scanner would use, prompting the question through the chat: "the automated scan, what payloads does it employ? do you define them upfront?". The following reply was made: "you don't, it actually uses logic to determine whether or not a payload is successful and it will tinker the payloads depending on the type of responses that it's getting.For example when trying different SQL injection payloads and depending on what response comes back, like if it finds a response that looks like a sql injection flaw, then it will include it to the list of the already found issues" Exploring the many options and the ways of launching an attack was happening too quickly for my liking. Fortunately, the webinar was being recorded, so afterwards I was able to replay that section and shed light on those grey areas. The PluginsLast explored were the Correlator and CO2 plugins, which showcased Burp's depth of extensibility, both written by Jason himself, who incidentally had a background in software engineering. CO2 is a suite inside the Burp Suite, comprised of miscellaneous and useful tools like the SQLMapper for automatic SQL injection discovery and exploitation; Laudanum for shell payloads like the PHP shell; User generator; Name mangler; CwEler etc.
The talk on plugins led the demonstration to an end, revealing that 2 hours had elapsed all too quickly and that it had been an exciting and entertaining experience. ConclusionSumming up, Burp is an elaborate suite worth getting to know and that, despite its UI intuitiveness, the sheer amount of options, menus and configurations could very easily overwhelm the uninitiated. While you can't single out an individual tool as being the most valuable since all are required to work together, we can at least identify the most frequently used ones - the Repeater, the Scanner and the Intruder. Another aspect of critical importance is getting to learn the workflow and the ways of monitoring the target and launching an attack. This knowledge cannot be conquered by merely taking part in a webinar but only after significant experience has been acquired, assimilated through further training, studying and practising. This webinar paves the way towards that goal. By spending most of its time focusing on the UI by sharing tips, tricks and gotchas it is necessarily light on the actual penetration testing workflow, a topic examined in more advanced webinars. However, it certainly serves as a basis for kick-starting an adventure into the field Follow Secure Idea's website for announcements of future presentations of the Tactical Burp Suite Webinar and make sure that you include it in your agenda.
More InformationSecure Ideas Tactical Burp Suite Webinar Related ArticlesEver Increasing Need For Secure Programming Heartbleed - The Programmer's View Cyber Warfare: Techniques, Tactics and Tools for Security Practitioners (Book Review)
To be informed about new articles on I Programmer, sign up for our weekly newsletter, subscribe to the RSS feed and follow us on, Twitter, Facebook, Google+ or Linkedin.
Comments
or email your comment to: comments@i-programmer.info
|
|||
| Last Updated ( Monday, 30 November 2015 ) |