| High-Tech, Cross-Browser Fingerprinting |
| Written by Nikos Vaggalis | |||
| Wednesday, 01 March 2017 | |||
|
Do you trust that getting rid of third party cookies keeps you safe from tracking? Think again as there's a new cross-browser tracking that can follow you no matter how often you delete cookies or switch browser. Nowadays, privacy issues arising from surfing the web are well known to the public and so are their countermeasures: cleaning your browser's cache, removing cookies, deleting history, installing ad-blockers and privacy aware extensions which reveal the trackers behind every page you visit. These are more or less the minimum of actions you can employ in feeling moderately safe. Of course there's much more you can do, such as Tor-enabled browsing, using a VPN or embrace the extremes of SilentKeys' Privacy Aware Keyboard. Nevertheless, all these measures fall within the realm of the superuser and are beyond the expertise of the general public. However there's a new technique that exploits other innocently leaked information by the browser in order to track your steps in cyberspace; a sophisticated approach which: utilizes many novel OS and hardware level features, such as those from graphics cards, CPU, and installed scripts. We extract these features by asking browsers to perform tasks that rely on corresponding OS and hardware functionalities. Because many of such OS and hardware level functions are exposed to JavaScript via browser APIs, we can extract features when asking the browser to perform certain tasks through these APIs.The extracted features can be used for both single- and cross-browser fingerprinting. The team of researchers from Lehigh University, in Bethlehem, Pennsylvania set out to investigate the possibility of using OS and hardware level features to track users not only within a single browser but also across different browsers on the same machine. The results are reported in (Cross-)Browser Fingerprinting via OS and Hardware Level Features presented this week at the 24th Annual Network and Distributed System Security Symposium NDSS 2017 which suggest further tracking techniques based on graphics and rendering which exploit the:
The researchers acquire access to these metrics through Javascript APIs running on the user's browser by getting it to perform various rendering tasks, similar to 3D benchmarking software, such as drawing curves and lines, which also include obtaining OS and hardware level information, the likes of screen resolution and timezone information. In the fingerprinting benchmarks that were performed there's a newsworthy gem - IE and Edge were the browsers with the highest leak rate, as such greater fingerprinting capability, when subjected to the single browser fingerprinting tests. The project is split into client and server parts, with the former involving approximately 14K lines of JavaScript, 1K lines of HTML, 2.4K lines of Coffeescript, while the latter has 3.7K lines of Python code encapsulated as an Apache server embedded module.
The source is open and available on GitHub.
Given that a demonstration is worth a thousand words, the authors have set up a website which you can visit and get your unique browser and machine emitted fingerprint. This opportunity was too good to miss and we subjected one of our own machines to it, by visiting the web page from both Firefox and Chrome.
Fingerprint of Chrome
The verdict was truly scary; a flawlessly identical machine level signature. It really does seem that your machine is the universal undeletable cookie that you cannot defeat.
More Information(Cross-)Browser Fingerprinting via OS and Hardware Level Features-Resarch Paper Uniquemachine-Online demonstration Related ArticlesSilentKeys A Privacy Aware Keyboard New Facebook Computer Vision Tags To be informed about new articles on I Programmer, sign up for our weekly newsletter, subscribe to the RSS feed and follow us on Facebook or Linkedin.
Comments
or email your comment to: comments@i-programmer.info |
|||
| Last Updated ( Wednesday, 01 March 2017 ) |
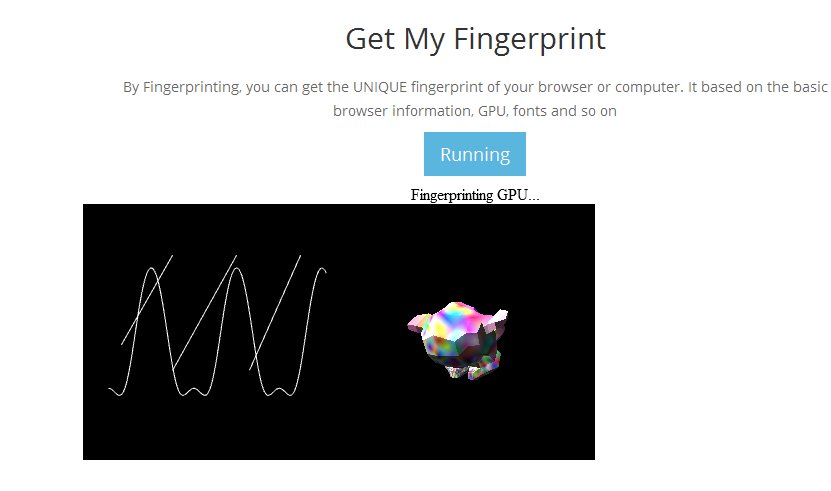 The browser, in order to fulfill these tasks calls into the OS, and the results are then converted into hashes so that they can be conveniently sent to the server. The server then collects the hashes sent over by each individual browser and algorithmically combines them to generate a unique machine cross-browser signature, with a confidence rate of over 99%.
The browser, in order to fulfill these tasks calls into the OS, and the results are then converted into hashes so that they can be conveniently sent to the server. The server then collects the hashes sent over by each individual browser and algorithmically combines them to generate a unique machine cross-browser signature, with a confidence rate of over 99%. 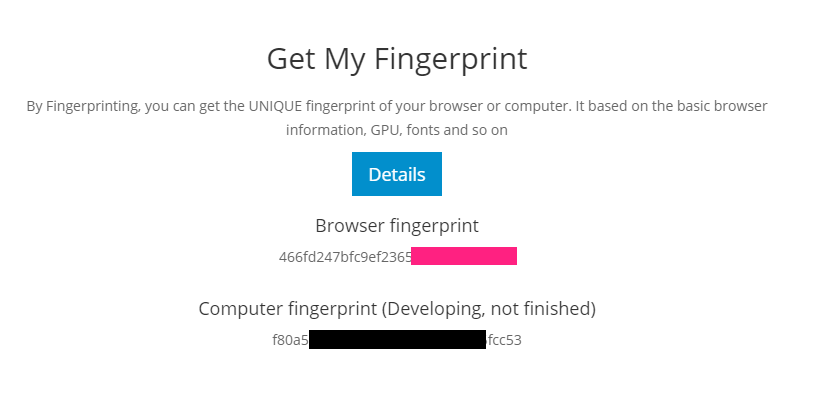
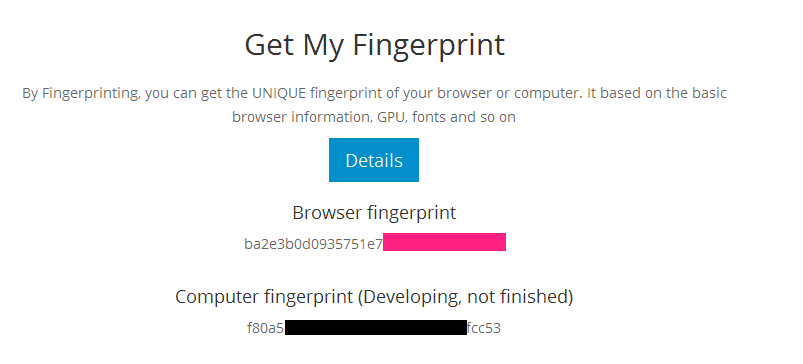 Fingerprint of Firefox
Fingerprint of Firefox 

