| Facebook Conceal Encryption For Android |
| Written by Mike James |
| Monday, 03 February 2014 |
|
Why is Facebook offering Android programmers an encryption library? The reason isn't clear, but it is open source so there can't be anything lurking in there, can there?
Facebook builds a lot of software and it open sources a pleasing amount of useful code. Conceal is a Java API targeting Android file encryption. It is designed to be efficient enough to be used on old Android devices with low memory and slower processors. Can you be sure that the crypto is done right? The good news is that there is no need to check out Conceal from the start because it doesn't actually implement the cryptographics algorithms. Instead it makes use of OpenSSL. This raises the question of why not just use OpenSS? The answer is that the entire OpenSSL library is sophisticated and flexible - and therefore big. Conceal ships with a subset of selected algorithms which makes it possible to fit everything into 85KB. Of course this means that you don't have the choice and flexibility that a full encryption library offers but, let's face it, you often don't need a choice - any encryption will satisfy the need.
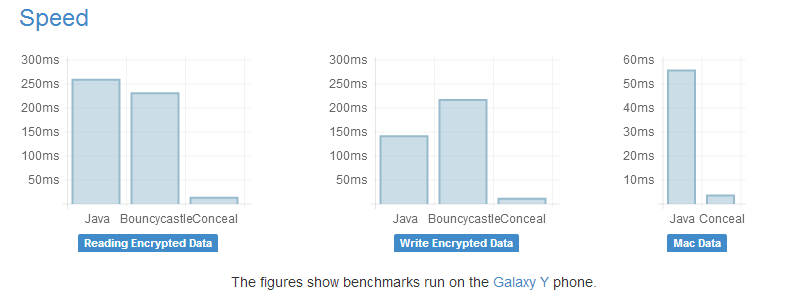
Comparing Conceal to Bouncycastle, another lightweight encryption library, and native Android encryption.
In this case Conceal make use of AES-GCM and HMAC-SHA1 which are faster versions of the standard algorithms and not available as part of OpenSSL on older Android devices. It also ships with a default keychain which stores the keys in SharedPreferences. In a real use of the library you would probably have to pay attention to implementing your own key management. What does Facebook use Conceal for? "Facebook currently uses Conceal to store image files on SD cards. Conceal helps Facebook protect user's private data by encrypting data stored on SD cards while allowing users to move some of the data storage needs of the app to the expandable SD card." Conceal is offered on a BSD licence, which means you can modify it, and the team are looking for help to expand and maintain the code.
More Information
Related ArticlesPrime Numbers And Primality Testing Stick Figure Guide To AES Encryption Public Key Cryptography Set To Fail In Five Years Android Security Hole More Stupid Error Than Defect Open Source Homomorphic Cryptography The Computer Science of Insecurity DARPA spends $20 million on homomorphic encryption 25 GPUs Crack Passwords In Minutes Security by obscurity - a new theory
To be informed about new articles on I Programmer, install the I Programmer Toolbar, subscribe to the RSS feed, follow us on, Twitter, Facebook, Google+ or Linkedin, or sign up for our weekly newsletter.
Comments
or email your comment to: comments@i-programmer.info
|
| Last Updated ( Monday, 03 February 2014 ) |