| Pwn2Own 2016 - The Results |
| Written by Alex Armstrong | |||||||||||||||||||||
| Monday, 21 March 2016 | |||||||||||||||||||||
|
Pwn2Own 2016 took place last week. As in previous years it was held at the CanSecWest conference held in Vancouver organised by the Zero Day Initiative, but following Trend Micro's acquisition of Tipping Point it was under the joint auspices of Hewlett Packard Enterprise and Trend Micro.
Another innovation for 2016 was the Master of Pwn award for the researcher who had the best overall performance over the two-day competition using a points system where the number of points reflects the difficulty of the exploit:
The ZDI announcement explained: For example, if someone has two successful entries (Google Chrome with a sandbox escape and Microsoft Edge with a SYSTEM escalation), the total points would be 28 points – and that’s in addition to the prize money itself. You'll notice that Firefox isn't in the list - this is because it is deemed too easy to hack. Announcing this change last month Brian Gorenc, manager of Vulnerability Research at HPE said: "'We wanted to focus on the browsers that have made serious security improvements in the last year." Another change to the mix was the introduction of VMware as a target. According to Brain Gorenc: Since it’s inception in 2007, Pwn2Own has increased the challenge level at each new competition, and this year is no different. While the latest browsers from Google, Microsoft, and Apple are still targets, the Windows-based targets will be running on a VMware Workstation virtual machine. A $75K bonus will be given to those who can escape the VMware virtual machine. This is our first year including VMware as a target, and we look forward to seeing what researchers will do with it.
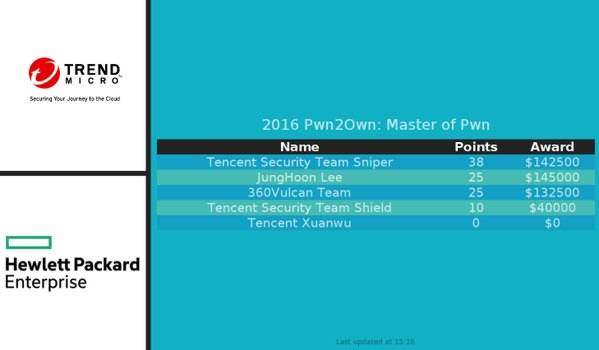
Pwn2Own 2016 attracted a record number of entrants but in the event less prize money was paid out than last year and none of the participants demonstrated a successful exploit for VMware. Over the two days a total of 21 bugs were successfully exploited distributed as below and a total of $460,000 USD bounty paid out to participating teams and individuals:
More details are given in these two videos:
At the end of the contest Tencent Security Team Sniper became Master of Pwn having earned the highest number of points (38). The team therefore earned an extra 65,000 ZDI points (worth $25,000) in addition to the $142,500 in cash awarded for its exploits. JungHoon Lee (lokihardt) left with the most money, $145,000. His exploits included a system-level code execution against Microsoft Edge using an uninitialized stack variable vulnerability in Edge and a directory traversal in Windows which earned him $85,000, the biggest cash prize awarded in a single attempt. The Trend Micro blog post summing up the event points out the value to the rest of us of this annual event and what this year's has revealed: As fun as the Pwn2Own competition is, ultimately it is serious business about understanding the current threats and weaknesses. This year’s competition succeeds in that regard. While it’s easy to focus on the state of browser security as shown at Pwn2Own, the real, important, technical story is about the state of kernel security. EVERY successful attack achieved SYSTEM or root privileges. This is a Pwn2Own first. It’s also a very worrying development. As ZDI researcher Jasiel Spelman noted, researchers and attackers are likely focusing on the kernel in response to advances in sandboxing. It’s a truism in security that when you harden one area, attackers and researchers will move their attention to another one. Based on Pwn2Own 2016, it appears that’s happening with a shift to focus on the kernel. This is also borne out by what we’re seeing in Linux lately: while Linux is outside the focus of Pwn2Own, we’ve seen a number of Linux kernel issues lately.
More InformationPwn2Own 2015: Day 2 and Event Wrap-Up Related ArticlesLargest Payout Ever At Pwn2Own 2015 Record Payouts At Hacking Contests Chrome Hacked Twice at CanSecWest Chrome Safe In Pwn2Own Contest
To be informed about new articles on I Programmer, sign up for our weekly newsletter, subscribe to the RSS feed and follow us on Twitter, Facebook or Linkedin.
Comments
or email your comment to: comments@i-programmer.info |
|||||||||||||||||||||
| Last Updated ( Thursday, 19 January 2017 ) |