| State of Software Security |
| Written by Janet Swift | |||
| Thursday, 03 December 2015 | |||
|
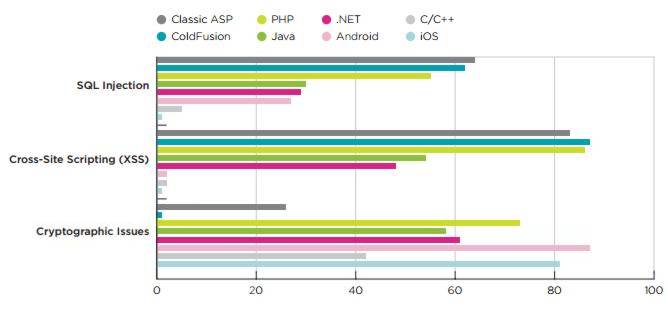
Veracode's report State of Software Security, launched today, focuses on application development and reveals that apps written in web scripting languages have a far higher prevalence rate of SQL injection and Cross-Site Scripting those written in .NET or Java. In his introduction to the report Veracode's CTO Chris Wysopal notes that the company's cloud based platform has now analyzed hundreds of thousands of applications and over 1.5 trillion lines of code and that the data it has amassed enables it to look at differing risks inherent in applications according to the language used and the method of their construction, advising: When organizations are starting new development projects and selecting languages and methodologies, the security team has an opportunity to anticipate the types of vulnerabilities that are likely to arise and how best to test for them. The main findings from the report are shown in this chart:
(Click in chart to enlarge)
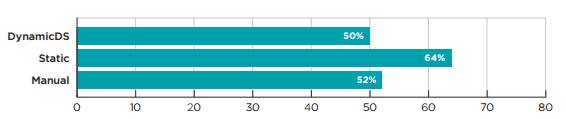
Applications written in web scripting languages have a far higher prevalence rate of vulnerability classes like SQL injection and Cross-Site Scripting than applications written in .NET or Java. In particular, 64 percent of applications written in Microsoft’s Classic ASP, 62 percent of applications written in ColdFusion, and 56 percent of applications written in PHP were observed to have at least one SQL injection vulnerability on initial assessment, compared to 29 percent of .NET applications and 21 percent of Java applications. Referring to the high vulnerability of PHP the report comments: One particular concern ..; is the high prevalence of PHP-based applications, thanks to the widespread adoption of content management system (CMS) frameworks like WordPress, Drupal and Joomla. According to some estimates, 74.6 million web sites use WordPress, and another few million use Drupal and Joomla. Noting that mobile applications had the highest rate of cryptographic issues, at 87 percent for Android and 80 percent for iOS the report states: This suggests that while mobile app developers may be aware of the need for cryptography to protect sensitive data and thus use it in their applications, few of them know how to implement it correctly. By looking at the fix rate, that is the number of vulnerabilities that were fixed divided by the total number found, Veracode reveals that static assessment is superior to both manual and dynamic methods.
On average fix 64 percent of static vulnerabilities get fixed, compared to 50 percent of dynamic vulnerabilities — on average, 28 percent better. The report states: There are several possible reasons why static analysis observed a higher fix rate. The most likely is that static provides higher fidelity data about the root cause of a vulnerability, including source file and line number. But there are other possibilities, including the likelihood that a static assessment is being run on an application that is actively under development and that engineering therefore already sees fixing issues as a priority, where dynamic assessments may be run on a production system where the development team may not be actively engaged. It also cautions: This is not to say that a security program should rely exclusively on static analysis. Some vulnerability classes can only be caught at runtime, using a technique like DAST, behavioral mobile app testing or interactive application self-testing. Some, like business logic vulnerabilities, require a skilled human tester.
More InformationState of Software Security: Focus on Application Development Related ArticlesTactical Pentesting With Burp Suite Ever Increasing Need For Secure Programming Heartbleed - The Programmer's View
To be informed about new articles on I Programmer, sign up for our weekly newsletter, subscribe to the RSS feed and follow us on, Twitter, Facebook, Google+ or Linkedin.
Comments
or email your comment to: comments@i-programmer.info
|
|||
| Last Updated ( Thursday, 03 December 2015 ) |