| How The Jeep Was Hacked |
| Written by Harry Fairhead | |||
| Sunday, 16 August 2015 | |||
|
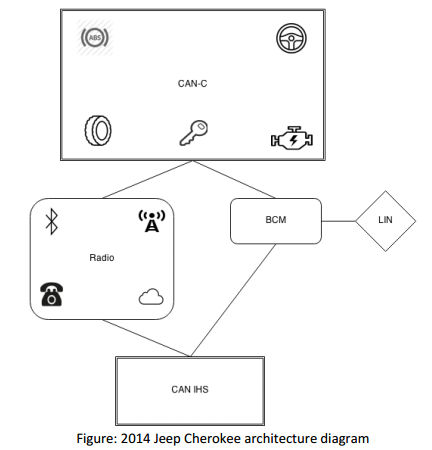
Now we have the story of exactly how the Jeep Cherokee was hacked so that it could be controlled remotely, a demonstration that ultimately led to a costly recall of 1.4 million vehicles. Cars are more like computers with an engine and some wheels. In this brief period between human assisted driving and completely autonomous driving we can begin to explore the security aspects. A number of car hacks have recently hit the news headlines, but it is only now that the technical details of the vulnerabilities are being made public at Black Hat USA 2015 in a paper by Charlie Miller and Chris Valasek. What is interesting is how weak the security was. For example, the initial attack was on the car's WiFi which used a password generated from the time of day the car's multimedia system was first activated. Given the precision of the time and date you would think that this was reasonable, but if you know the month the car was manufactured you can bring the possibilities down to 15 million. Add to this the fact the car was most likely activated during the day and you are down to 7 million. In fact, the password wasn't actually generated on the time but the default time January 01 2013 00.00 GMT plus a few seconds that the multimedia unit took to boot. This reduces the number of combinations to tens and very very easy to crack. At this point the hackers could connect to the multimedia computer and after a few simple exploits gain control of it. Of course, this only allowed them to turn the radio on, change channels and volume, but it still could be a driver distraction. Tracking the car using the GPS did prove possible, however. Soon afterwards the hackers also found a way to gain access via the Sprint Cellular network. The real challenge was in finding a way out of the sandbox that the multimedia system is in. Most of the interesting electronics in a car is connected together via a CAN bus - a simple serial bus that lets the engine sensors talk to the control computer the ECU. The CAN bus on all cars is the focus of security measures, which mainly amount to keeping it isolated from the outside world - what has become known as an "air gap". Unfortunately this air gap didn't really exist.
The Jeep has two CAN buses - one for the engine and one for the other systems. The multimedia controller wasn't on either of the CAN buses, but it was connected to a chip that was. The chip in question was programmed only to listen to the CAN bus and not to send commands over it. So in its basic setup you could argue that there was an "air gap" in that there was no way for the multimedia controller to send messages via the intermediate device. Of course we all know that programmable chips can be programmed and this was the next stage in the hack. Reverse engineering the software of the intermediate chip made it possible to flash the chip with a new program, which did allow a bidirectional connection to the CAN bus. At this point you can see that it's all over for the JEEP. The CAN bus gave access to just about everything. It was possible to control the steering wheel, brakes, transmission and lots of non critical things like the windscreen wipers and air con. If I had to pick one amazing "feature" is that the brakes could be bled while the car was moving slowly if a diagnostic session could be established - so effectively making them useless for stopping the car. The demonstration that all this is not theoretical was on Wired reporter Andy Greenberg's Jeep. At first it might have been just irritating: "Though I hadn’t touched the dashboard, the vents in the Jeep Cherokee started blasting cold air at the maximum setting, chilling the sweat on my back through the in-seat climate control system. Next the radio switched to the local hip hop station and began blaring Skee-lo at full volume. I spun the control knob left and hit the power button, to no avail. Then the windshield wipers turned on, and wiper fluid blurred the glass. As I tried to cope with all this, a picture of the two hackers performing these stunts appeared on the car’s digital display: Charlie Miller and Chris Valasek, wearing their trademark track suits. A nice touch, I thought."
However, soon after, things became more serious: "That’s when they cut the transmission. Immediately my accelerator stopped working. As I frantically pressed the pedal and watched the RPMs climb, the Jeep lost half its speed, then slowed to a crawl. This occurred just as I reached a long overpass, with no shoulder to offer an escape. The experiment had ceased to be fun." The holes have been patched so this shouldn't happen again - on the Jeep Cherokee at least. To quote from the paper, which is worth reading for the fine details of the struggle that the researchers faced: "This paper was a culmination of three years of research into automotive security. In it, we demonstrated a remote attack that can be performed against many Fiat-Chrysler vehicles. The number of vehicles that were vulnerable were in the hundreds of thousands and it forced a 1.4 million vehicle recall by FCA as well as changes to the Sprint carrier network. This remote attack could be performed against vehicles located anywhere in the United States and requires no modifications to the vehicle or physical interaction by the attacker or driver. As a result of the remote attack, certain physical systems such as steering and braking are affected. We provide this research in the hopes that we can learn to build more secure vehicles in the future so that drivers can trust they are safe from a cyber attack while driving. This information can be used by manufacturers, suppliers, and security researchers to continue looking into the Jeep Cherokee and other vehicles in a community effort to secure modern automobiles."
More InformationRemote Exploitation of an Unaltered Passenger Vehicle (pdf) Wired: Hackers remotely kill a Jeep on the highway - with me in it. Related ArticlesRobot cars - provably uncrashable? Planes are Unix hosts waiting to be hacked To be informed about new articles on I Programmer, install the I Programmer Toolbar, subscribe to the RSS feed, follow us on, Twitter, Facebook, Google+ or Linkedin, or sign up for our weekly newsletter.
Comments
or email your comment to: comments@i-programmer.info |
|||
| Last Updated ( Sunday, 16 August 2015 ) |