| Microsoft Edge Falls Victim At Pwn2Own |
| Written by Sue Gee | ||||||||||||||
| Wednesday, 22 March 2017 | ||||||||||||||
|
This year's 10th anniversary Pwn2Own spanned over thee days rather than the previous two and was won by the team from 360 Security who achieved a full virtual machine escape through Microsoft Edge.
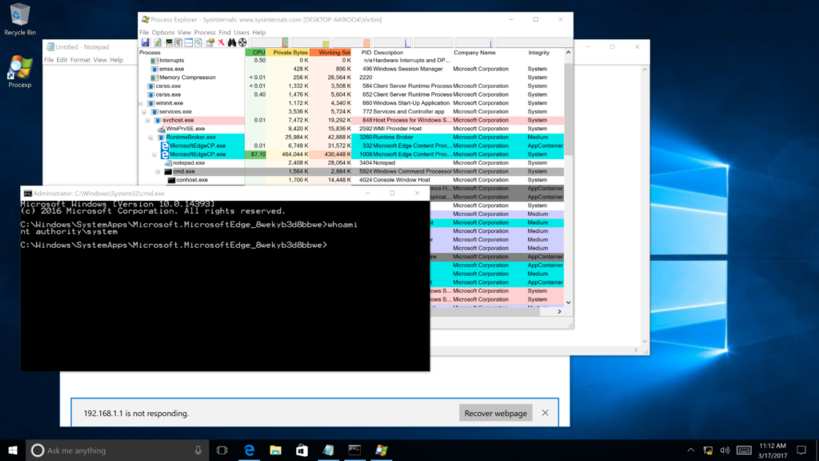
This impressive feat was described by Dustin Childs on the TrendMicro account of the contest as "a first for the Pwn2Own competition" and it earned the team $105,000 and 27 Master of Pwn points. Explaining the exploit in an e-mail, Qihoo 360 Executive Director Zheng Zheng, wrote: "We used a JavaScript engine bug within Microsoft Edge to achieve the code execution inside the Edge sandbox, and we used a Windows 10 kernel bug to escape from it and fully compromise the guest machine Then we exploited a hardware simulation bug within VMware to escape from the guest operating system to the host one. All started from and only by a controlled a website." If this wasn't enough bad news for Microsoft, in the very next exploit Richard Zhu (fluorescence) targeted Edge with a SYSTEM-level escalation. Although his first try failed, his made a second attempt using two separate use-after-free (UAF) bugs in Edge and then escalated to SYSTEM using a buffer overflow in the Windows kernel. This was rewarded with $55,000 and 14 points towards Master of Pwn. Earlier in the contest two Tencent Secuirty teams had overcome Edge security. Team Ether gained $80,000 and 10 points by using an arbitrary write in Chakra to escape the sandbox using a logic bug within the sandbox and Team Sniper (Keen Lab and PC Mgr) completed their exploit of Microsoft Edge with a UAF in Chakra and escalated to SYSTEM-level privileges through a UAF in the Windows kernel which won them $55,000 and 14 points towards Master of Pwn. In its attempt to get Windows 10 users to adopt Edge as their browsers, Microsoft had been relying on the idea that Edge was superior to Chrome - which emerged from Pwn2Own 2017 unscathed - in terms of both secuurity and speed.
Now Microsoft has dropped the "Microsoft Edge is safer than Chrome" from its list of Tips on Window 10 machines. Today the list consists only of the "faster than Chrome" item. Safari was successfully exploited by the duo Samuel Groß and Niklas Baumstark, by 360 Security and by Chaitin Security Research Lab, which was making its first appearance at Pwn2Own. Mozilla Firefox was another of its victims which it attacked with an integer overflow and escalated privileges through an uninitialized buffer in the Windows kernel. This earned them $30,000 and 9 Master of Pwn points.
Last year's Pwn2Own winners and this year's runner up, Tencent Security – Team Sniper (Keen Lab and PC Mgr), achieved the final exploit of the contest, which earned them $100,000 and 13 points. They used a three-bug chain to win the Virtual Machine Escapes (Guest-to-Host) category with a VMWare Workstation exploit. This involved a Windows kernel UAF, a Workstation infoleak, and an uninitialized buffer in Workstation to go guest-to-host and was made more difficult because VMware Tools were not installed in the guest:
Announcing the final results, Dustin Childs writes: We saw a record 51 bugs come through the program. We paid contestants $833,000 USD in addition to the dozen laptops we handed out to winners. And, we awarded a total of 196 Master of Pwn points. Here’s the breakdown of the top five contestants:
The final day was certainly the most exciting and you can see the highlights in this video:
More InformationResults-Pwn2Own 2107 Day-Three Results – Pwn2Own 2017 Day Two Results – Pwn2Own 2017 Day One Related ArticlesGet Ready for Expanded Pwn2Own 2017 Largest Payout Ever At Pwn2Own 2015 To be informed about new articles on I Programmer, sign up for our weekly newsletter, subscribe to the RSS feed and follow us on Twitter, Facebook or Linkedin.
Comments
or email your comment to: comments@i-programmer.info |
||||||||||||||
| Last Updated ( Friday, 29 March 2019 ) |