| Your Android Could Leak Data Via USB Charging |
| Written by Harry Fairhead | |||
| Tuesday, 20 September 2016 | |||
|
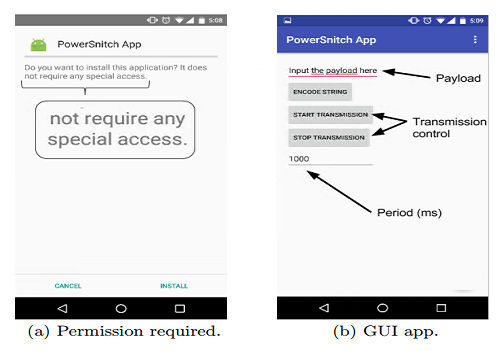
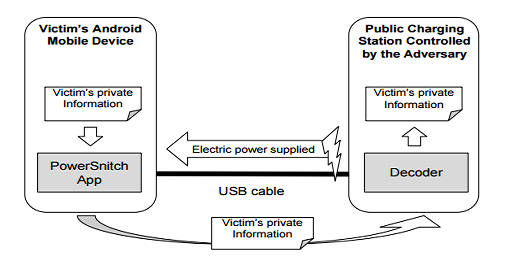
Security researchers have invented a way to get data out of any mobile device using nothing but a USB charging point without the need for a serial connection or any special permissions. This is an interesting but possibly unlikely way you could get covert data out of a mobile phone or similar device using just the charging characteristics via a USB port. The idea is simple enough, but it requires that some software is installed on the device and the USB charger has to be modified. The USB charger measures the charge current. The software, PowerSnitch, checks to make sure that the device is charging and the screen is off and then modulates the power consumption by giving the CPU things to do. The charger decodes the current changes to a bit pattern. Notice that this means that the device doesn't need to be connected to a full USB with serial communication enabled - all the data is transferred over a charging link. The abstract from the paper tells it all: More and more people are regularly using mobile and battery-powered handsets, such as smartphones and tablets. At the same time, thanks to the technological innovation and to the high user demands, those devices are integrating extensive functionalities and developers are writing battery-draining apps, which results in a surge of energy consumption of these devices. This scenario leads many people to often look for opportunities to charge their devices at public charging stations: the presence of such stations is already prominent around public areas such as hotels, shopping malls, airports, gyms and museums, and is expected to significantly grow in the future. While most of the time the power comes for free, there is no guarantee that the charging station is not maliciously controlled by an adversary, with the intention to exfiltrate data from the devices that are connected to it. In this paper, we illustrate for the first time how an adversary could leverage a maliciously controlled charging station to exfiltrate data from the smartphone via a USB charging cable (i.e., without using the data transfer functionality), controlling a simple app running on the device, and without requiring any permission to be granted by the user to send data out of the device. We show the feasibility of the proposed attack through a prototype implementation in Android, which is able to send out potentially sensitive information, such as IMEI, contacts' phone number, and pictures.
We implemented a proof-of-concept app, PowerSnitch, that can send out bits of data in the form of power bursts by manipulating the power consumption of the device’s CPU. Interestingly, PowerSnitch does not require any special permission from the user at install-time (nor at run-time) to exfiltrate data out of the smartphone over the USB cable. On the adversary’s side, we designed and implemented a decoder to retrieve the bits that have been transmitted via power bursts. Our empirical results show that we can successfully decode a payload of 512 bits with a 0% Bit Error Ratio (BER). In addition, we stress that the goal of this paper is to assess for the first time the feasibility of data transmission on such a covert channel and not to optimize its performance, which we will tackle as future work. The bottom line is, should we be worried? Probably not. There are so many ways to get data out of a system and to make this work you need a compromised public charging station and mobile phones with your app installed, presumably under the cover ??of a different app. It is difficult to think up a scenario where this is easy to arrange. A company would have to set up to supply public charging points and offer access via a contaminated app, which seems like a lot of trouble to go to.
Even so the number of covert channels for data out of a device seems to grow. More InformationNo Free Charge Theorem: a Covert Channel via USB Charging Cable on Mobile Devices Related ArticlesSilentKeys A Privacy Aware Keyboard Identifying Programmers From Executable Binaries Your Phone's Battery Leaks - Your Id That Is WebRTC Leaks Local IP Addresses Cat Photos - A Potential Security Risk? Print Me If You Dare - the Rise of Printer Malware Security by obscurity - a new theory
To be informed about new articles on I Programmer, sign up for our weekly newsletter, subscribe to the RSS feed and follow us on, Twitter, Facebook, Google+ or Linkedin.
Comments
or email your comment to: comments@i-programmer.info
|
|||
| Last Updated ( Tuesday, 20 September 2016 ) |
 If you would like more details of how well it worked:
If you would like more details of how well it worked: