| Microsoft Bug Bounty Extends Scope |
| Written by Alex Armstrong | |||
| Tuesday, 04 October 2016 | |||
|
Microsoft recently added NET Core and ASP.NET Core to its suite of ongoing bounty programs. It has also expanded its Remote Code Execution Bounty for Microsoft Edge. The .NET Core and ASP.NET Core program started on September 1, 2016 with the following key points:
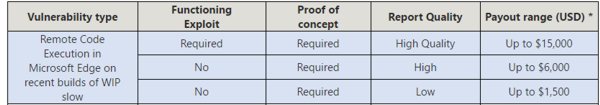
A bounty for RCE (Remote Code Execution) vulnerabilities in Microsoft Edge on Windows Insider Preview builds was introduced on August 4, 2016 and runs until May 15, 2017. Initially it offered the following rewards: Vulnerabilities in open source sections of Chakra are also included in the program. At the end of September it was extended with the MSRC Team explaining: Since security is a continuous effort and not a destination, we prioritize acquiring different types of vulnerabilities in different points of time. Currently, we are focusing on vulnerabilities that lead to violation of W3C standards that compromise privacy and integrity of important user data, and RCEs. As a result rewards are available for reporting Same Origin Policy (SoP) bypass vulnerabilities, for example UXSS, and referrer spoofs with proof of concept, i.e.the files and steps necessary to reliably reproduce the vulnerability. A bounty of up to $6,000 will be paid in the case of a high quality report or up to $1,500 in the case of a low quality report. Microsoft's highest level of reward is for Mitigation Bypass Bounty and Bounty for Defense Program, initiated in 2013. Submitting a novel mitigation bypass against the latest Windows platform can earn up to $100,000 with a further $100,000 on offer for a defense technique to block it. The highest payout to date has been $125,000 in 2015. So far in 2016 7 payouts, ranging from $5,000 to $100,000 and totalling $245,000, have been made. Bounties of between $500 and $15,000 are also regularly paid as part of the Microsoft Online Services Bug Bounty program. There were 30 recipients of such bounties in the first two quarters of 2016 but while their names are listed on the Bounty Hunters Honor Roll, the amounts awarded are not supplied. Stay turned to the Microsoft Security Response Center blog for further updates to the Microsoft Bug Bounty programs.
More InformationAnnouncing a Microsoft .NET Core and ASP.NET Core Bug Bounty Update to the Microsoft Edge Web Platform on Windows Insider Preview Bug Bounty Program terms Related ArticlesMicrosoft Doubles Bounty Payouts Microsoft Offers $100,000 For Novel Exploits New Online Services Bug Bounty Program Microsoft Expands Bounty Programs Bounty Hunter Awarded $100,000 To be informed about new articles on I Programmer, sign up for our weekly newsletter, subscribe to the RSS feed, or follow us on Twitter, Facebook, Google+ or Linkedin.
Comments
or email your comment to: comments@i-programmer.info
|
|||
| Last Updated ( Tuesday, 04 October 2016 ) |