| Passcodes prove predictable |
| Written by Kay Ewbank | |||
| Tuesday, 28 June 2011 | |||
|
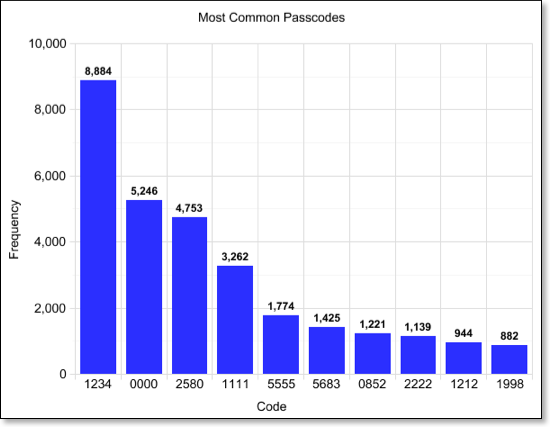
Just 10 different passcodes would be enough to unlock one in seven iPhones, according to research by a developer of apps for the iPhone. Daniel Amitay blogged how he anonymously gathered passcodes for his Big Brother iPhone app, and making the assumption that his customers would use the same passcode as they did for their iPhone, came up with the statistic that 15% of all passcode sets were represented by only 10 different passcodes (out of a possible 10,000). As Amitay says, ‘the implication is that a thief (or just a prankster) could safely try 10 different passcodes on your iPhone without initiating the data wipe. With a 15% success rate, about 1 in 7 iPhones would unlock - even more if the intruder knows the user's years of birth, relationship status and so on." Amitay’s Big Brother Camera Security app (which has now been dropped from the appstore because Apple isn’t very happy with what Amitay has been doing) has a passcode setup screen and lock screen that are nearly identical to those of the actual iPhone passcode lock. He extrapolated that the collected information would closely correlate with actual iPhone passcodes - not necessarily the case, as users may well be more careful with more ‘important’ passcodes.
Source: http://amitay.us/blog/files/most_common_iphone_passcodes.php
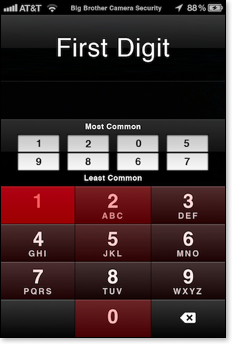
The information gathered was worryingly predictable. As the above graph shows, out of 204,508 recorded passcodes, the top ten most common were 1234, 0000, 2580, 1111, 5555, 5683, 0852, 2222, 1212, and 1998. Which is a very depressing list indeed if you are concerned about user security. Most of these codes follow formulae such as four identical digits, moving in a line up or down the pad, or repetition. If you’re wondering about 5683, it’s the numeric representation of ‘L-O-V-E’ on your phone (aaaahhh). Other common passwords in the top 50 were probable birth or graduation years - 1980-2000. If you also look at the frequency of each digit chosen you find that the entropy only increases as the digit order goes on. That is the most used first digit is one, the most used second digit is two with only the third and fourth digits looking anything like an even spread across the choices. What this means is that of a four digit pin only the final two digits are actually serving their full purpose.
So how do you make sure the users of your applications have strong passwords? It’s an interesting question, and one that has been problematic ever since passwords and codes were invented. You could, on the basis of this and similar research, do a check for the most common options and not allow them, but that isn’t going to make you popular with your customers. There again, they’re not going to be overjoyed if their passwords and codes can be guessed as easily as this research suggests. Problems, problems.
If you would like to be informed about new articles on I Programmer you can either follow us on Twitter or Facebook or you can subscribe to our weekly newsletter.
|
|||
| Last Updated ( Tuesday, 28 June 2011 ) |