| Intel Extends Bug Bounty Program |
| Written by Alex Armstrong | |||
| Friday, 16 February 2018 | |||
|
To support its Security-First Pledge made as a response to Meltdown and Spectre, Intel is opening up its Bug Bounty Program to all security researchers, raising bounty awards and offering a new program focused specifically on side channel vulnerabilities.
The Intel® Bug Bounty Program was launched in March 2017 but up until now was an invitation-only scheme. According to its HackerOne page, since its inception $93,000 has been paid out with an average bounty of $5,000; 14 reports have been resolved and thanks extended to 15 security researchers. When Brian Kzanich published his open letter on January 11, his assurance was: By Jan. 15, we will have issued updates for at least 90 percent of Intel CPUs introduced in the past five years, with updates for the remainder of these CPUs available by the end of January. We will then focus on issuing updates for older products as prioritized by our customers. This is a commitment that has proved impossible to fulfill and in his announcement of the expansion of the Bug Bounty Program, Rick Echevarria notes that moving from an invitation-only program to one that is open to all security researchers will significantly expanding the pool of eligible researchers. Under the revised program the main requirements for participation in the program are:
There are the usual exclusions about not being on the US list of sanctioned individuals or being resident of a US-embargoed country and that neither you or any family or household member can have been working for Intel or one of its subsidiaries within 6 months. In addition you have to agree to participate in testing mitigation effectiveness and coordinate disclosure/release/publication of your finding with Intel. To be eligible for Bounty Award consideration, a report must identify an original and previously unreported and not publicly disclosed vulnerability and must be encrypted with the Intel PSIRT public PGP key, available at https://security-center.intel.com/PGPPublicKey.aspx. A report must include clear documentation on the vulnerability and instructions on how to reproduce the vulnerability and needs to include your assessed CVSS v3 vector string, score, and rating using one of two approved CVSS v3 calculators.
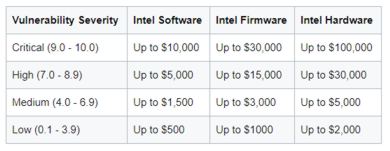
To make this worthwhile this is the new schedule of award in which Intel Software, Firmware, and Hardware are all in scope. You'll notice that the highest rewards, up to $100,000 are for vulnerabilities in Intel Hardware which includes the following:
The Intel Firmware encompassed by the program, attracting bounties of up to $30,000, includes::
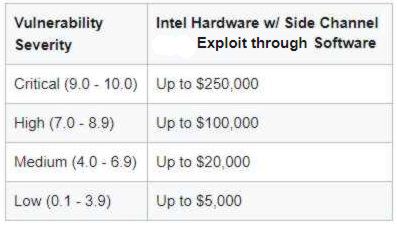
while device drivers, applications and tool count as software with rewards up to $10,000,. Note, however, that vulnerabilities already known to Intel, or in pre-release versions and versions no longer under active support are excluded. The new limited duration program focused specifically on side channel vulnerabilities that are root-caused to Intel Hardware and exploitable via software runs until l December 31, 2018. The award for disclosures under this program is up to $250,000:
Again the harder a vulnerability is to mitigate, the more Intel will pay.
More InformationRelated ArticlesMicrosoft and Facebook Launch Internet Bug Bounty Scheme Microsoft Bug Bounty Extends Scope
To be informed about new articles on I Programmer, sign up for our weekly newsletter, subscribe to the RSS feed and follow us on Twitter, Facebook or Linkedin.
Comments
or email your comment to: comments@i-programmer.info |
|||
| Last Updated ( Friday, 16 February 2018 ) |