| Airship, a truly secure PHP CMS |
| Written by Nikos Vaggalis | |||
| Thursday, 08 September 2016 | |||
|
Attacks on popular Content Management Systems are all too common, and with hacking nowadays considered big business, there's no sign of the attacks declining. CMSs therefore find themselves caught in the eye of the storm, considered as a prime target for both script kiddies and professional hackers alike, as they hold the biggest share of the e-commerce market. The statistics revealed in Sucuri's most recent Website Hacked Trend report, paint a depressing picture, mainly due to the great user adoption of CMS which ...brings about serious challenges to the internet as a whole as it introduces a large influx of unskilled webmasters and service providers responsible for the deployment and administrations of these sites This by itself does not speak of the security vulnerabilities inherently found in the CMSs themselves; just take a look at the ever growing CVE (Common Vulnerabilities and Exposures) lists pertaining to three popular frameworks: and if you add to that the latest and rising trend in ransomware the situation quickly becomes much scarier. So what are the options here, how to go about it? Certainly, employing a number of best practices as well as common sense, such as monitoring the CVE listings or patching and upgrading the systems, do help, but they're not panacea since not everybody is, or can be, educated in following them. Then, there's the option of the security reviews and pen testing, which are both expensive and down to skilled pros, although anyone hosting a web site should at least be familiar with XSS.Thankfully, we have already taken care of that part by reviewing and suggesting two great educational services, Hacksplaining and XSShunter. The other and better option, which goes directly to the source of the problem is to fix the infrastructure, the CMS itself. Let's start out with a hardened CMS which can sufficiently protect its user's from the very beginning. Let's take heed of the most popular CMS's bad parts and use them as the reference point to base upon. That is exactly what has been done by Airship, a secure open source PHP CMS developed by Paragon Initiative Enterprises. But what is meant by secure, how secure is it and why is it more secure than the others? Paragon has apparently done its homework and took a deep look into the good but also bad parts of the big three, Wordpress, Joomla and Drupal, as outlined in the report On the (in)security of popular open source Content Management Systems written in PHP,which compares them against the merits of its own Airship CMS. From that report, we've extracted the ugly keypoints, since they're those of more interest: Security wise
Joomla doesn't offer automatic security updates. In the event that a security vulnerability is discovered in Joomla and a fix is released, it's up to every individual Joomla site operator to validate and install the update manually. Until the patch is applied, your systems are vulnerable. As a consequence, most Joomla websites still run outdated versions of Joomla Then,the one that does, does so insecurely. WordPress's automatic updates are not cryptographically signed with (an offline) private key. This means if an attacker can compromise their update servers and upload a malicious download, they can install a trojan on 26.6% of the websites on the Internet.
Furthermore, WordPress developers proudly boast that WordPress powers 1 in 4 websites, and pride themselves on supporting unsupported versions of PHP as a "usability" feature rather than a security liability that could potentially break the Internet for everyone At the end of the day, there are two ways to solve this dilemma: Paragon opted for the latter and urges you too.
These cover the bare minimum, but then there's also:
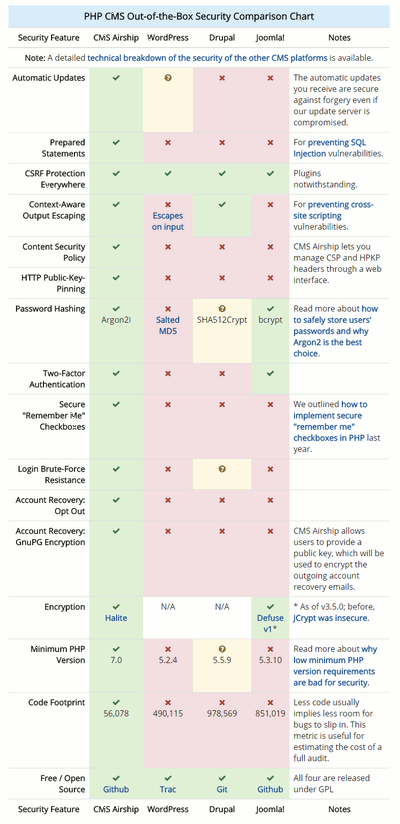
and the list goes on. There's a most helpful side-by-side comparison chart that in a glance demonstrates Airship's strong points in comparison to the shortcomings of the other CMS's.
What's even more intriguing is that in case Tor is installed, Airship can proxy all network requests over it, thus preventing the server's IP address from being revealed.
CMS Wise Airship's structure is similar to that of MVC, it is just the terminology that differs; the Model is called Blueprint, the View is called Lens (in essence being template files rendered by Twig) while the Controller is referred to as the Landing. Customization is facilitated by the Gears system, which provides an interface to the core classes themselves, and allows for their tailoring at runtime. Then there's
Installation The minimum requirements are :
Airship can also run as a dockerized image via docker-compose. Version 1.3.0 was released on August 29, and as still in its infancy steps, bugs, issues and to-dos should be something natural to stumble upon.Nevertheless as a Github project it is open to contribution, be it coding, documentation, security analysis, end user testing, etc.The first tutorials should soon appear as revealed in this open issue. That leaves us with the question of whether Airship does in fact hold the answer to a more secure web. It certainly looks as though the potential is there, but until it has wide spread adoption we can't be sure.
More InformationOn the (in)security of popular open source Content Management Systems written in PHP Keyggdrasil, Continuum, and the Cryptography Powering CMS Airship The PHP Security Platinum Standard: Raising the Bar with CMS Airship (side-by-side comparison) Sucuri Website Hacked Trend report
Related ArticlesTactical Pentesting With Burp Suite
To be informed about new articles on I Programmer, sign up for our weekly newsletter,subscribe to the RSS feed and follow us on, Twitter, Facebook, Google+ or Linkedin.
Comments
or email your comment to: comments@i-programmer.info
|
|||
| Last Updated ( Thursday, 08 September 2016 ) |